Всем привет!!!
В этот раз я расскажу как быстро и легко настроить VPN сервер на Synology NAS, что бы иметь доступ к своей домашней или офисной сети находясь за ее пределами.
Для чего нужен такой VPN сервер для дома? Причин может быть много. Это либо безопасность, что бы не открывать незащищенные порты наружу открывая только порты VPN сервера, либо просто что бы подключаться к домашним устройствам из вне, так как буд-то вы находитесь дома. Для офиса же или предприятия думаю такой вопрос излишний, любой администратор понимает суть VPN сервера.
И так у вас есть Synology NAS, вы заходите в центр пакетов и ставите VPN server
Открываете его и видите такую картину:
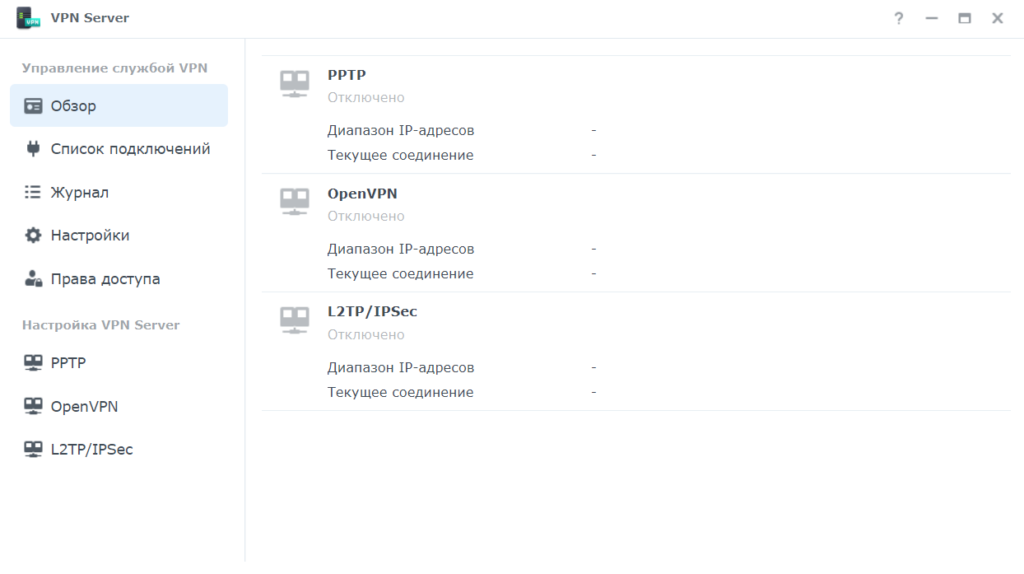
Synology VPN server поддерживает три протокола: PPTP, OpenVPN и L2TP\IPsec. PPTP хороший протокол, но считается менее безопасным чем другие. OpenVPN это открытый протокол и он есть на большинстве устройств. А L2TP\IPsec считается самым защищенным из представленных и он встроен почти во все ОС и устройства Windows, MAC OS, Android и IOS. Именно поэтому я и решил использовать последний, так как не нужно устанавливать дополнительное ПО.
Настройка L2TP\IPsec выглядит очень просто:
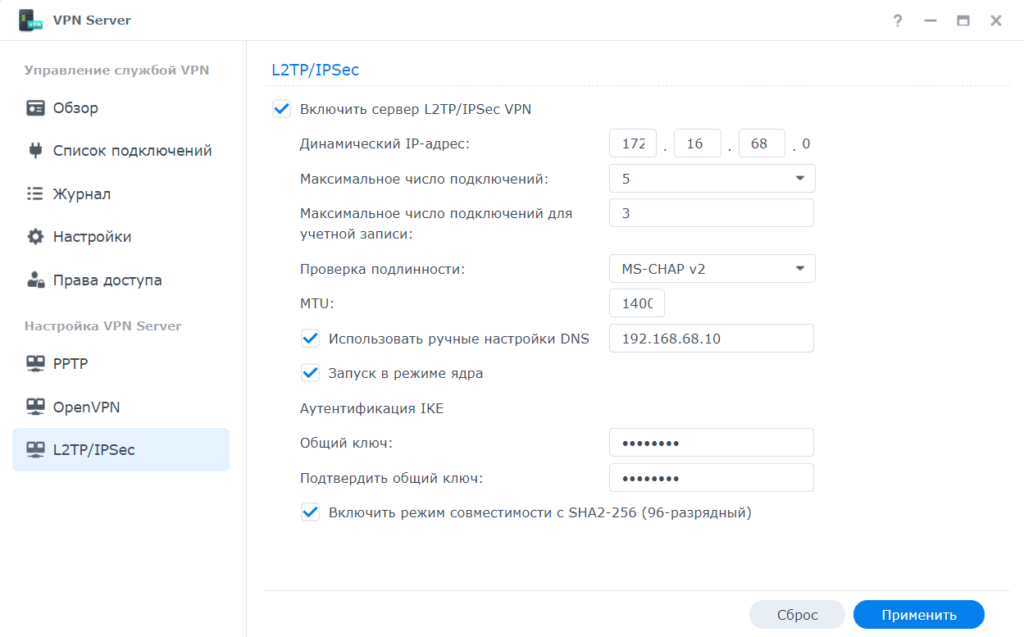
- Динамический IP-адрес, VPN Server присвоит VPN-клиентам IP-адреса, выбрав их из диапазона виртуальных IP-адресов. Например, если для динамического IP-адреса сервера VPN Server задано значение «172.16.68.0», то виртуальный IP-адрес VPN-клиента может быть в диапазоне от « 172.16.68.1» до « 172.16.68.[максимальное число подключений]» для PPTP и в диапазоне от « 172.16.68.2» до « 172.16.68.255» для OpenVPN.
Важно! Прежде чем указывать динамический IP-адрес сервера VPN, учтите следующее.
- Динамические IP-адреса, разрешенные для сервера VPN Server, должны быть в одном из следующих диапазонов:
- От «10.0.0.0» до «10.255.255.0»
- От «172.16.0.0» до «172.31.255.0»
- От «192.168.0.0» до «192.168.255.0»
- Указанные динамический IP-адрес сервера VPN Server и присвоенные клиентам VPN виртуальные IP-адреса не должны конфликтовать с IP-адресами, которые сейчас используются в вашей локальной сети.
Простыми словами сетка для VPN должна отличаться от вашей существующей реальной сети.
- С максимальным числом подключений думаю все понятно.
- В проверке подлинности два варианта, тот что PAP передает пароли в незашифрованном виде, это нас не устраивает, поэтому выбираем MS-CHAP v2
- MTU 1400 стоит по умолчанию, рекомендую так же оставить, так как оно должно быть меньше чем реальное MTU интернет подключения. Так как мы его не знаем, то ставим 1400. Этот параметр точно подойдет и особо не повлияет ни на что.
- Если вы хотите что бы через VPN подключение еще и ваш личный DNS работал, то укажите его IP адрес
- Запуск в режиме ядра ставим для максимальной производительности VPN сервера.
- Очень важно задать общий ключь достаточно сложный, это влияет на безопасность.
- Включать или не включать режим совместимости это на ваше усмотрения.
Для подключения MAC OS галочку совместимости нужно убрать !!!
На этом вся настройка Synology VPN сервера выполнена и он готов к подключению первых клиентов.
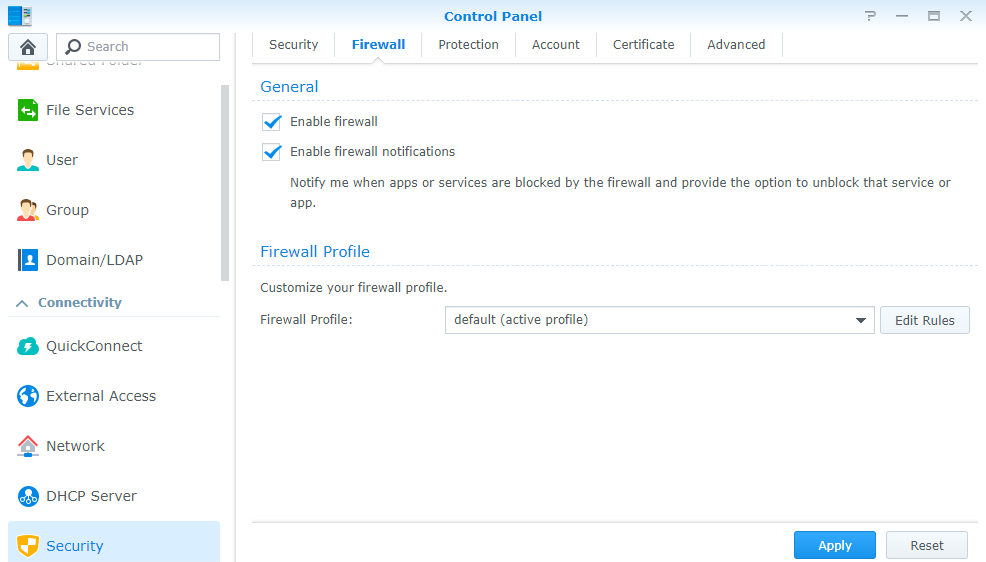
Так же хочу отметить, что если у вас на Synology настроен фаервол, то нужно разрешить в нем сетку для динамического IP настроенную первым этапом и открыть порты для внешних подключений
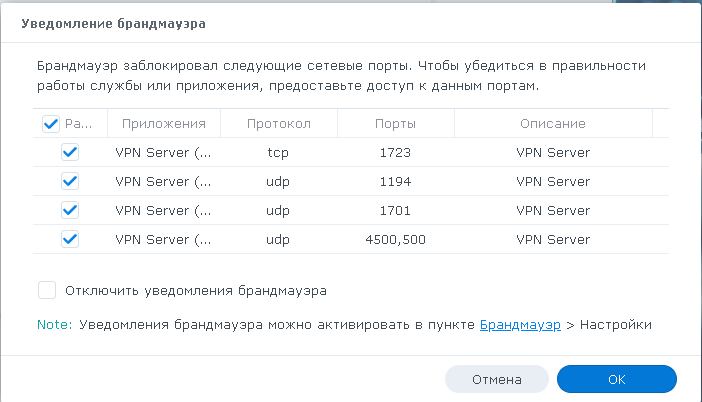
Порт 1723\TCP нужен для PPTP, порт 1194\UDP нужен для OpenVPN, а порты 1701\UDP, 4500\UDP и 500\UDP нужны для L2TP\IPsec.
Впрочем, когда вы все настроите и нажмете применить вам это сообщит система:
Windows 10\11 клиент
Теперь, когда все настроено и порты открыты и проброшены на NAT, настало время подключиться к нашему VPN серверу, Начнем с Windows. А с ним и только с ним как раз есть небольшие трудности.
По умолчанию встроенный VPN клиент Windows не поддерживает подключение к L2TP/IPsec через NAT. Дело в том, что IPsec использует протокол ESP (Encapsulating Security Payload) для шифрования пакетов, а протокол ESP не поддерживает PAT (Port Address Translation). Если вы хотите использовать IPSec для коммуникации, Microsoft рекомендует использовать белые IP адреса на VPN сервере. Простыми словами Windows хочет что бы вы поднимали VPN сервер на роутере или на сервере, который подключен непосредственно к интернету без роутера и NAT. Это весьма дорого и не всегда выполнимо. Поэтому есть решение.
Можно использовать командлет PowerShell для внесения изменений в реестр:
Set-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Services\PolicyAgent" -Name "AssumeUDPEncapsulationContextOnSendRule" -Type DWORD -Value 2
Или отредактировать реестр вручную. Более подробно Как подключиться к VPN Server от Synology с помощью ПК Windows? – Центр знаний Synology
Затем создадим подключение VPN с такими параметрами:
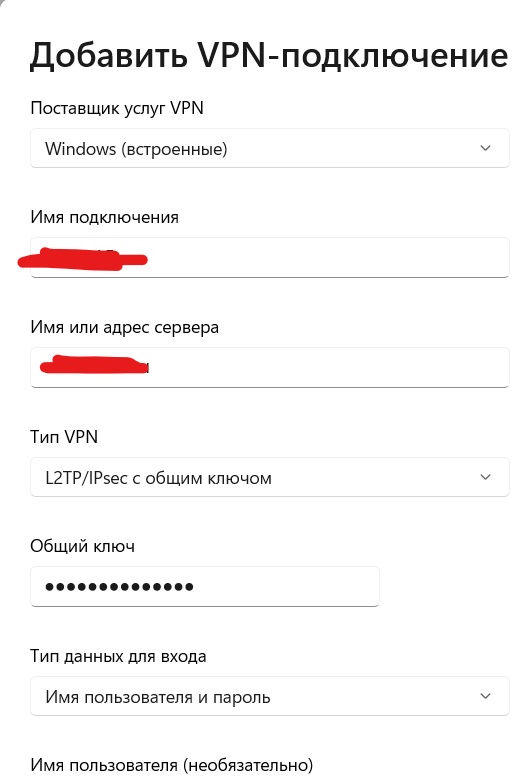
На этом настройка подключения на Windows завершена и можно подключаться.
Если способ выше не помогает и ваш Windows ПК не подключается по L2TP то нужно сделать следующее:
Взято от сюда: Исправляем проблему подключения к L2TP/IPSec VPN серверу за NAT | Windows для системных администраторов (winitpro.ru)
- Ослабляет уровень шифрования, для L2TP/IPSec используются алгоритмы MD5 и DES:
reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters" /v AllowL2TPWeakCrypto /t REG_DWORD /d 1 /f
- Включает шифрование IPsec, которое часто отключается некоторыми VPN клиентами или утилитами:
reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters" /v ProhibitIpSec /t REG_DWORD /d 0 /fЕсли и это не поможет, то используйте вместо L2TP протокола PPTP на крайний случай.
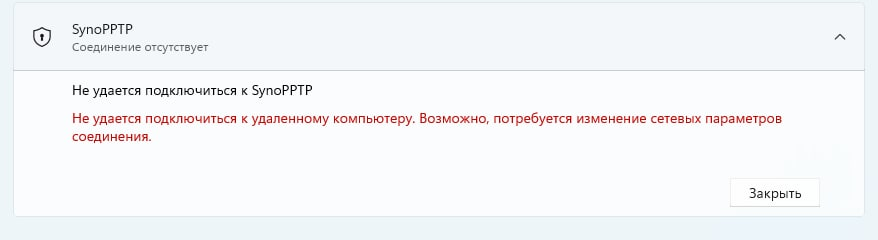
Так же на Windows ПК встречается такая проблема: Не удается подключиться к удаленному компьютеру. Возможно потребуется изменение сетевых параметров соединения
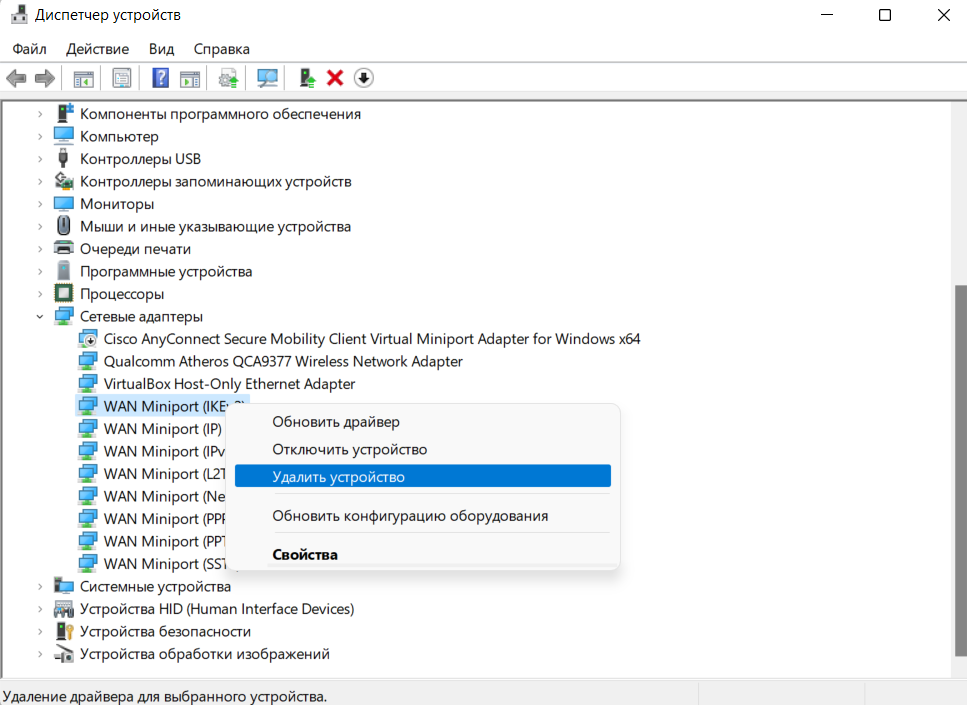
Нужно открыть Диспетчер устройств – Сетевые адаптеры и удалить все устройства WAN Miniport
Затем щелкнуть в самый верх по названию вашего ПК и нажать кнопку “Обновить конфигурацию оборудования”
Устройства WAN miniport будут установлены заново и проблем с подключением не будет.
На телефоне подключение выглядит практически также, не вижу смысла это расписывать. Тут самое главное, то что это легко и все необходимое уже встроено в телефон. Настраивается в пару действий и работает просто превосходно.
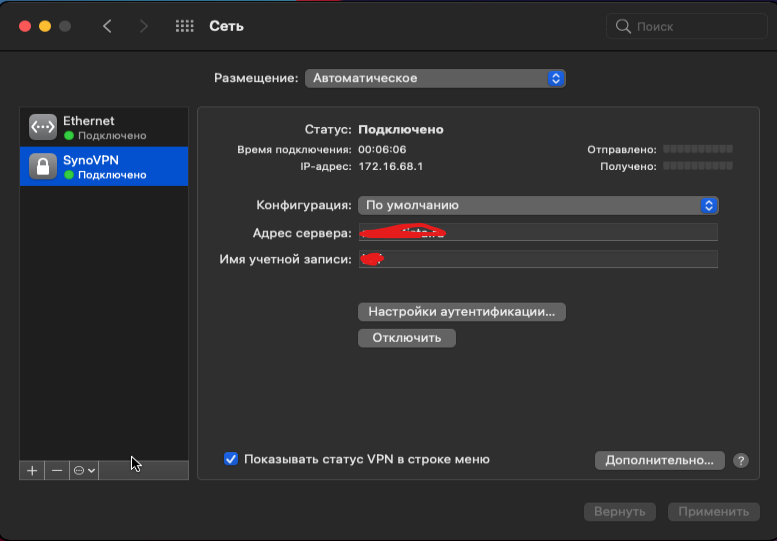
MAC OS клиент
На MAC OS тоже все просто, только выглядит по другому, а параметры все теже:
Linux клиент
Мой основной и самый любимый дистрибутив для декстопа это Ubuntu. Поэтому буду показывать на ее примере, но в других дистрибутивах будет оналогично.
Для начала установим требуемый пакет, которого почему-то нет по умолчанию
sudo apt install network-manager-l2tp network-manager-l2tp-gnomeПосле этого открываем настройки, сетевые подключения и жмем добавить VPN
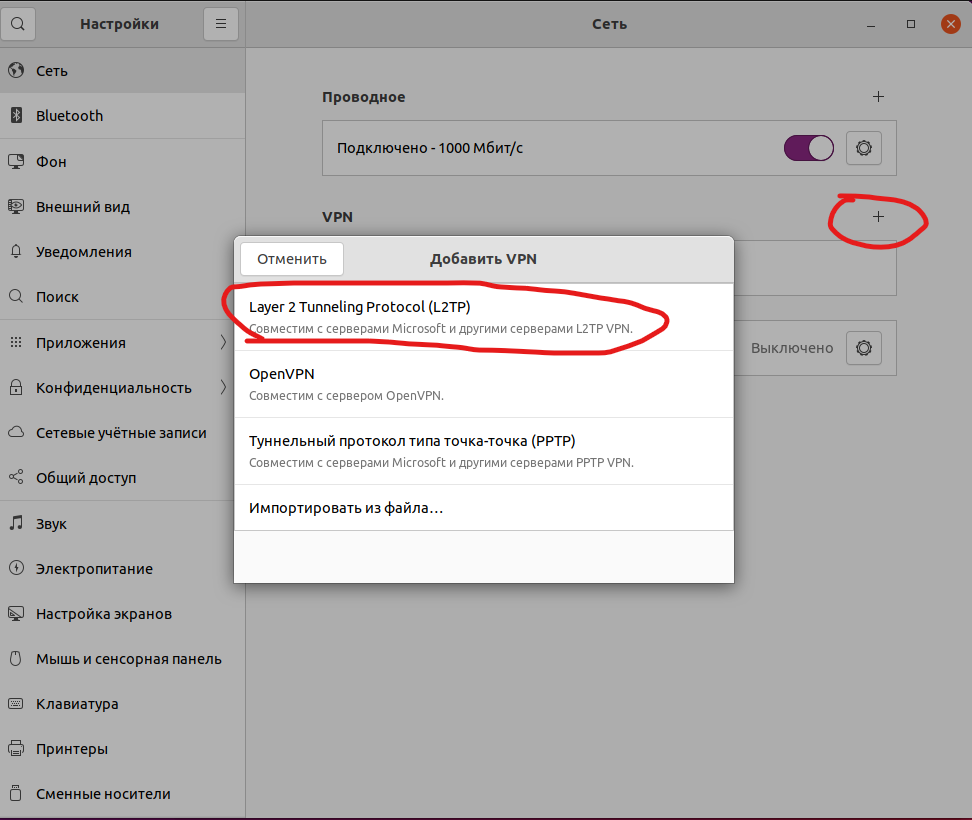
В открывшемся окне указываем название, доменное имя вашего NAS или IP адрес, логин DSM и тут начинается интересное
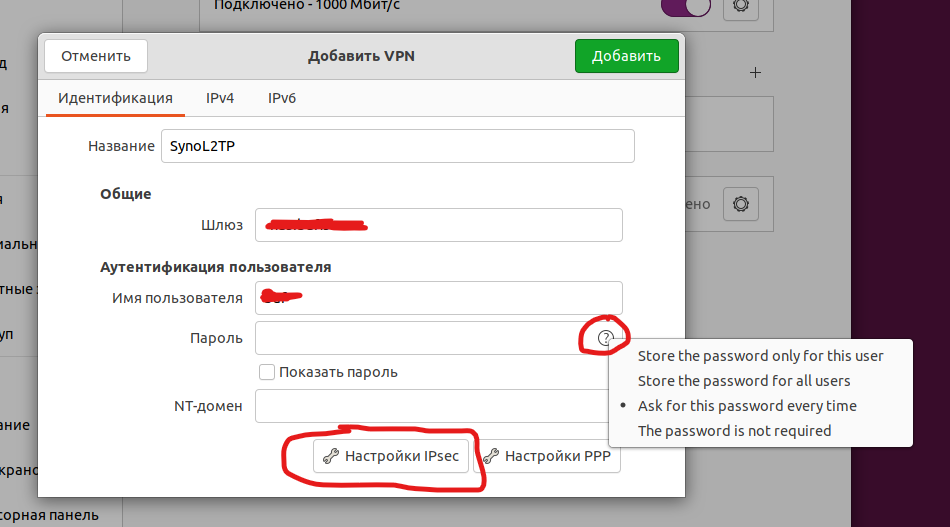
По умолчанию пароль вы не введете, нажимаем на вопрос и выбираем пункт 1 или 2 (сохранять пароль дя пользователя или всей ОС). Я выбрал первое. Затем жмете на кнопку Настройка Ipsec и вводите общий ключь сервера
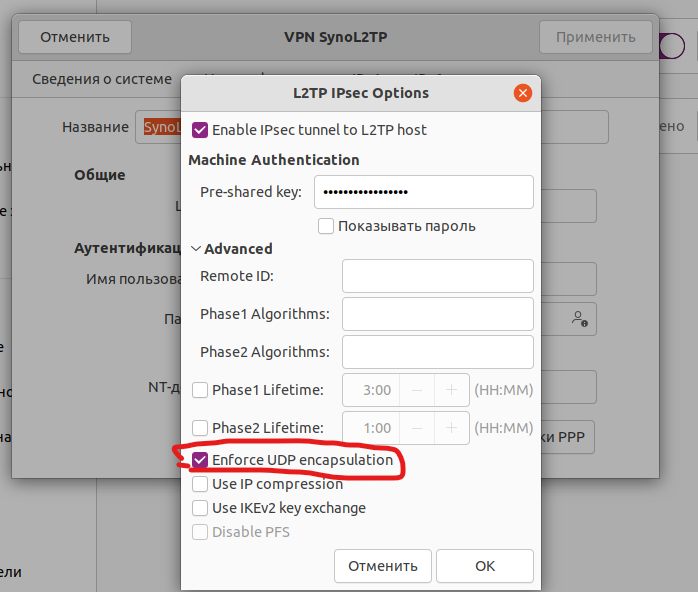
Так же обязательно открывайте дополнительные настройки и ставте галочку: Enforce UDP encapsulation
Сохряняем все настройки, и включаем VPN. Если все введено правильно, то в терминале можно увидеть VPN интерфейс ну и проверить, что все работает как надо.
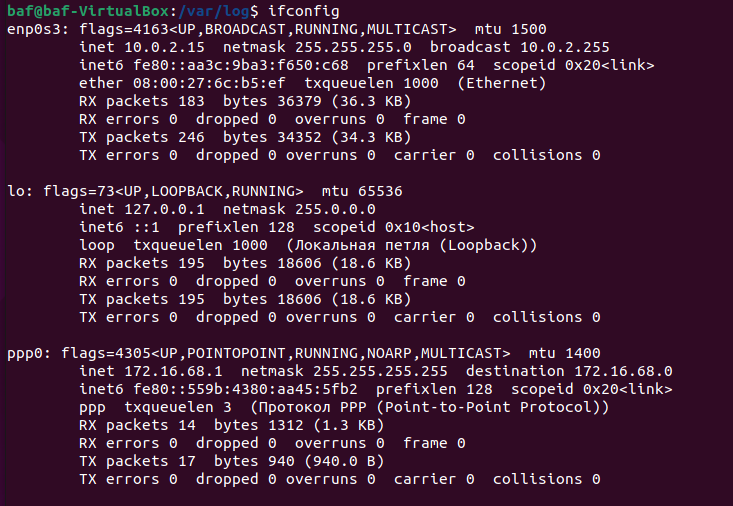
На этом моя статья “Synology NAS поднимаем VPN сервер” завершена. Пользуйтесь Synology и желаю удачи!!!
Время на прочтение
3 мин
Количество просмотров 12K
Всем привет!
Знаю, что тем с настройками OpenVPN сделано множество. Однако, сам столкнулся с тем, что систематизированной информации по теме заголовка в принципе нет и решил поделиться опытом в первую очередь с теми, кто не является гуру в администрировании OpenVPN, но хотел бы добиться подключения удаленных подсетей по типу site-to-site на NAS Synology. Заодно и для себя заметку оставить на память.
Итак. Есть NAS Synology DS918+ с установленным пакетом VPN Server, настроенным OpenVPN и пользователями, которые могут коннектиться к VPN серверу. Не буду вдаваться в подробности настройки сервера в интерфейсе DSM (веб портал NAS сервера). Эта информация есть на сайте производителя.
Проблема в том, что интерфейс DSM (на дату публикации версия 6.2.3) имеет ограниченное количество настроек для управления OpenVPN сервером. В нашем случае требуется схема соединения по типу site-to-site, т.е. хосты подсети клиента VPN должны видеть хосты подсети VPN сервера и наоборот. Типовые настройки, доступные на NAS, позволяют настроить доступ только от хостов подсети клиента VPN до хостов подсети сервера VPN.
Для настройки доступа к подсетям клиентов VPN из подсети VPN сервера нам понадобится зайти на NAS через SSH и настроить файл конфигурации OpenVPN сервера вручную.
Для редактирования файлов на NAS по SSH мне удобнее пользоваться Midnight Commander. Для этого я в Центре пакетов подключил источник packages.synocommunity.com и установил пакет Midnight Commander.
Заходим по SSH на NAS под учетной записью с правами администратора.
Набираем sudo su и ещё раз указываем пароль администратора:
Набираем команду mc и запускаем Midnight Commander:
Далее переходим в каталог /var/packages/VPNCenter/etc/openvpn/ и находим файл openvpn.conf:
По задаче нам необходимо подключить 2 удаленные подсети. Для этого заводим через DSM 2 учетные записи на NAS с ограниченными правами на все службы NAS и выдаём доступ только на VPN подключение в настройках VPN Server. Для каждого клиента нам нужно настроить статичный IP выделяемый VPN сервером и роутинг через этот IP трафика с подсети VPN сервера на подсеть VPN клиента.
Исходные данные:
Подсеть VPN сервера: 192.168.1.0/24.
Пул адресов OpenVPN сервера 10.8.0.0/24. Сам OpenVPN сервер получает адрес 10.8.0.1.
Подсеть VPN клиента 1 (пользователь VPN): 192.168.10.0/24, должен получать на OpenVPN сервере статичный адрес 10.8.0.5
Подсеть VPN клиента 2 (пользователь VPN-GUST): 192.168.5.0/24, должен получать на OpenVPN сервере статичный адрес 10.8.0.4
В каталоге настроек создаем папку ccd и неё создаём файлы настроек с названиями, соответствующими логинам пользователей.
Для пользователя VPN в файле прописываем следующие настройки:
Для пользователя VPN-GUST в файле прописываем следующие:
Остаётся только поднастроить конфигурацию OpenVPN сервера — добавить параметр для чтения настроек клиентов и добавить роутинги на подсети клиентов:
В приведенном скриншоте первые 2 строчки конфига настраиваются с помощью интерфейса DSM (простановка галки на параметре «Разрешить клиентам осуществлять доступ к локальной сети сервера» в настройках OpenVPN сервера).
Строка client-config-dir ccd указывает, что настройки клиентов находятся в папке ccd.
Далее 2 строки настройки добавляют роуты на подсети клиентов через соответствующие шлюзы OpenVPN.
И наконец для правильной работы необходимо применить топологию subnet.
Все остальные настройки в файле не трогаем.
После прописывания настроек не забываем перезагрузить сервис VPN Server в менеджере пакетов. На хостах или шлюзе для хостов подсети сервера прописать роуты на подсети клиентов через NAS.
В моём случае шлюзом для всех хостов подсети, в которой находится NAS (его IP 192.168.1.3), выступал роутер (192.168.1.1). На этом роутере я добавил в статическую таблицу маршрутов записи маршрутизации для сетей 192.168.5.0/24 и 192.168.10.0/24 на шлюз 192.168.1.3 (NAS).
Не забываем, что при включенном брандмауэре на NAS необходимо будет настроить и его. Плюс на клиентской стороне может быть включен брандмауэр, который так же нужно будет настроить.
ПС. Я не являюсь профессионалом в сетевых технологиях и в частности в работе с OpenVPN, просто делюсь своим опытом и публикую настройки, которые я сделал, позволившие настроить связь между подсетями по типу site-to-site. Возможно есть и более простая и/или правильная настройка, буду только рад, если поделитесь опытом в комментариях.
In this tutorial, we will look at the Synology NAS OpenVPN setup and configuration instructions.
After my recent Ultimate Synology NAS Setup & Configuration Guide tutorial, I received a ton of great feedback from users who were interested in safely and securely accessing their NAS from outside of their network.
I’ve been using OpenVPN on a Synology NAS using VPN Server for the past year and have had no issues at all. I can safely access my NAS anywhere in the world and more importantly, I control access.
I will quickly explain what a VPN server does and the different types of VPN server configurations, but if you already know, you can skip down to the OpenVPN Server instructions for the Synology NAS.
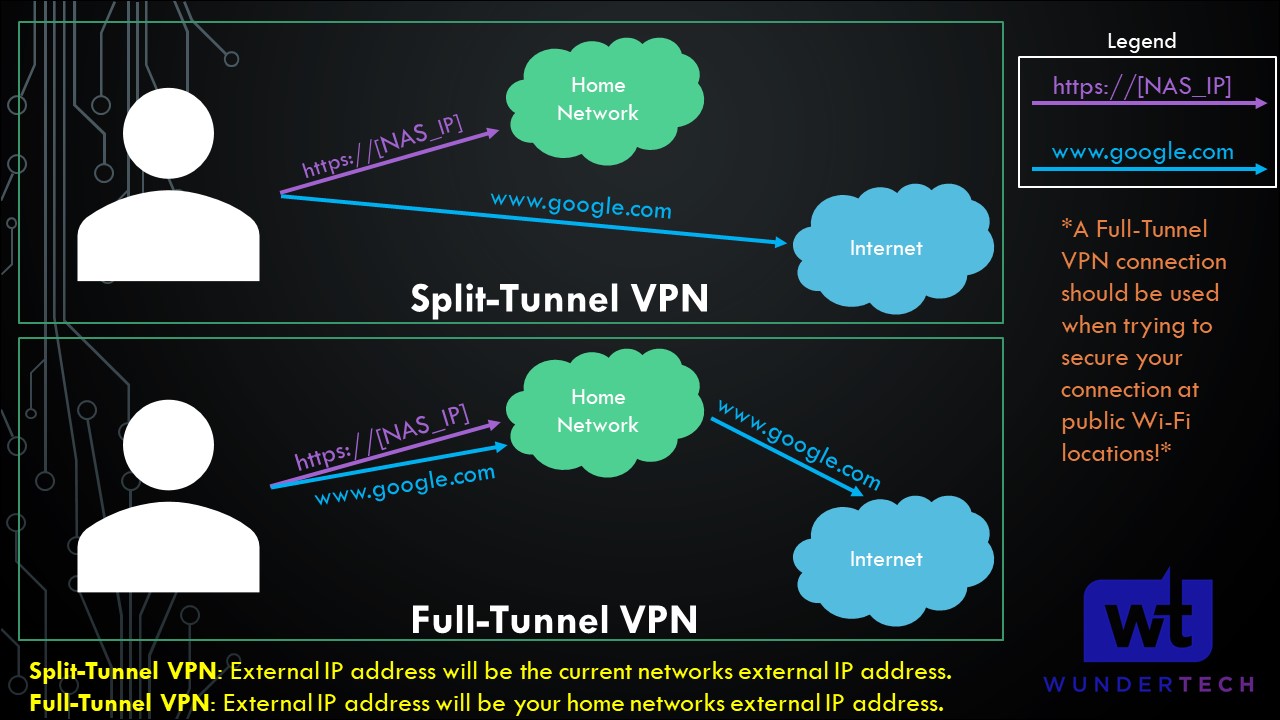
VPN Server Description & VPN Connection Types
A VPN is a Virtual Private Network that extends your private network to a public network. In layman’s terms, it allows you to securely connect back to your local network from an outside network. There are two types of VPN networks:
Split-Tunnel VPN: Traffic is only sent through your network if it is attempting to access an internal resource. Your IP address when navigating to a site outside of your network will be the IP address of the network that you are currently on.
Full-Tunnel VPN: All traffic is sent through your home network. Your IP address for internal and external requests will be your home networks.
I created a very basic image below that explains this, but we will look at how to configure both in later steps. It’s important to note that both connection types will allow you to access your local network. This only shows how traffic is routed differently to external networks.
NOTE: This is not the exact network flow. I am simplifying the process as much as I can.
The steps below should be followed to install and configure Synology’s OpenVPN Server following best practices.
Step 1: Install OpenVPN Package on a Synology NAS
The screenshots below are from DSM 6, but work exactly the same way on DSM 7.
- Open the Package Center and Install the VPN Server application.
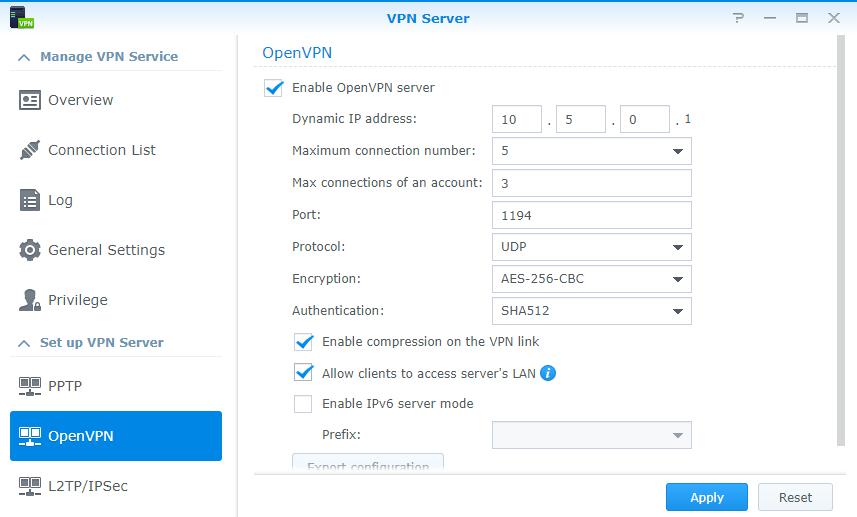
- Open the application and navigate to the OpenVPN section.
- Enable OpenVPN Server. Change the Dynamic IP address range and maximum connection properties if you’d like. Since we are trying to access our Synology NAS outside of our network, we need to enable Allow clients to access server’s LAN. The rest can stay as default. Click Apply.
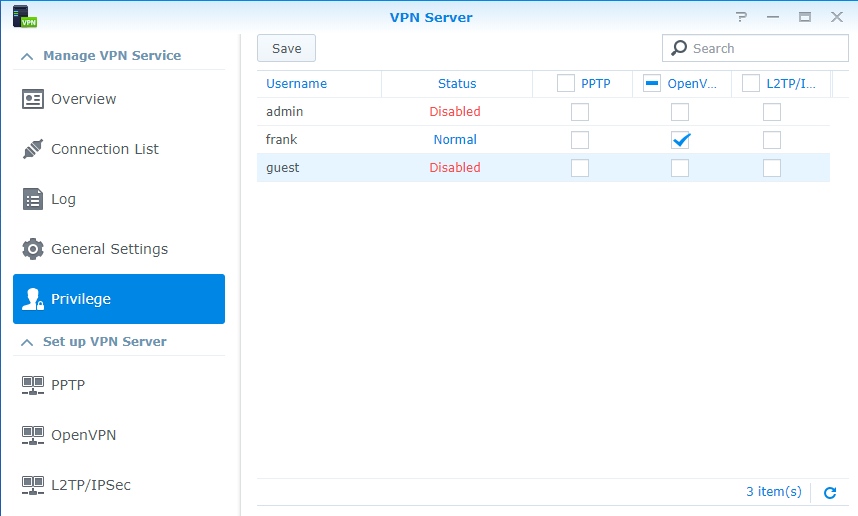
- Navigate to the privilege section and ensure that the user account that you’d like to connect to the VPN with has permission for OpenVPN.
Step 2: Configure Synology’s Firewall
Our VPN Server is now configured, but we need to ensure that our firewall allows access to UDP port 1194. If you aren’t sure how to configure Synology’s Firewall, you can learn how in our Ultimate Synology NAS Setup & Configuration Guide.
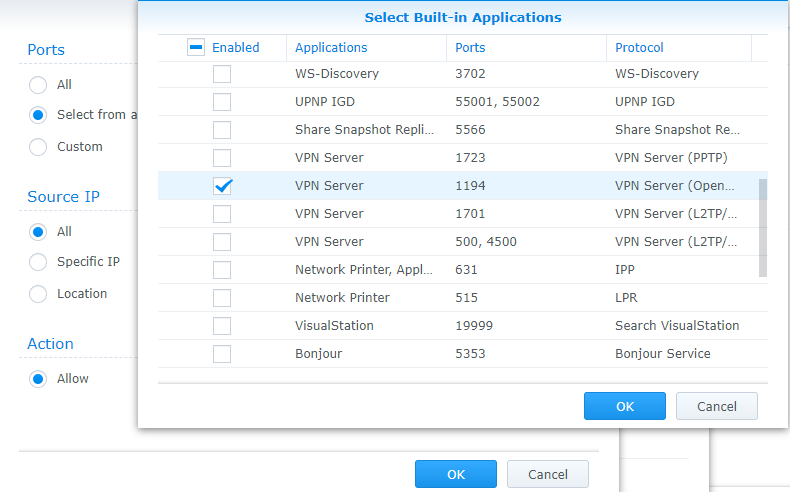
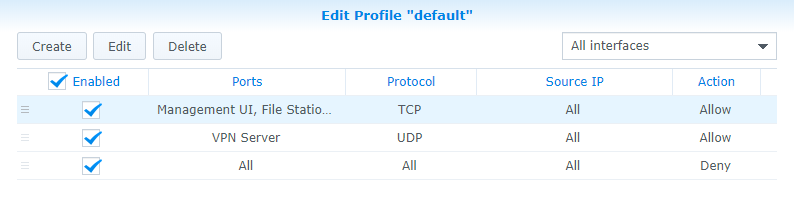
- If you are using Synology’s firewall, open the Control Panel, Security, then navigate to the Firewall and Edit Rules.
- Create an Allow rule for the VPN Server (OpenVPN) application, UDP port 1194.
- When completed, the rule should be above the deny all rule.
Step 3: Port Forwarding for OpenVPN
We just configured our Synology firewall to allow connections on UDP port 1194 so that we can connect to OpenVPN on a Synology NAS.
We now need to port forward UDP port 1194 on our router to our Synology NAS. Synology has UPnP functionality, which gives your NAS the ability to open ports on your router automatically. If you have a UPnP compatible router, it’s very easy to set this up.
However, there is a lot of debate on the security of UPnP, so I will not be going over it in this tutorial. If you’d like to do it this way, you can read Synology’s help article here.
Now, port forwarding will be completely different on every brand’s router settings page. This is a great guide that shows how to port forward on a few different brands of routers, but the best thing to do is try and google the name of your router and port forwarding. Example: Netgear port forwarding
This process requires you to have a static IP address setup. If you don’t currently have a static IP address setup, read how to set up a static IP address here.
- Create a port forwarding rule for UDP port 1194 to your Synology NAS’s IP address. In the example below, 192.168.1.220 is the IP address of my Synology NAS.
Assuming that you were able to open UDP port 1194 and configure the Synology firewall rule successfully, the port configuration is now complete!
Step 4: Modifying the OpenVPN Configuration File
Now that we have configured OpenVPN on a Synology NAS, we need to modify our configuration file. Before we get into the steps, you need to ensure that you have DDNS configured.
Most people have dynamic external IP addresses, so creating a DDNS hostname is required because you need to ensure that you are always accessing your external IP address.
If you’d like to configure DDNS using a free synology.me hostname, you can follow Synology’s instructions here. If you’d like to use DuckDNS, I wrote up a tutorial on how you can do it here.
If you are absolutely positive that you have a static external IP address that never changes, you do not have to set up DDNS. Simply use your external IP address as YOUR_SERVER_IP.
It’s also important to note that the DDNS provider is irrelevant, you just need to ensure that you have a DDNS hostname configured!
- Open the VPN Server application and select OpenVPN. Select Export configuration.
- Extract the contents of the folder. We will only be editing the Synology NAS OpenVPN .ovpn file, so open that file with a text editor.
- By default, you will receive a default Synology NAS OpenVPN configuration file with a unique certificate at the bottom. This document shouldn’t be shared with anyone other than users who you would like to authenticate with your VPN. We need to change the items below that are highlighted in red.
- YOUR_SERVER_IP: This should be the DDNS hostname that you configured.
- redirect-gateway def1: This is what determines if you are configuring a split-tunnel or full-tunnel VPN. If you aren’t sure which you’d like, reference the image above to see the differences. I create two separate configuration files (one for split-tunnel and one for full-tunnel) and depending on the situation, use one or the other. To enable full-tunnel, remove the “#” sign (this is the symbol for a comment). Just removing the comment symbol will enable the full-tunnel VPN.
- NOTE: If you are using an iPhone and have iOS 7 or above, you will need to add redirect-gateway ipv6 under redirect-gateway def1.
- dhcp-option: If you have a local DNS server that you’d like to use, you can add the IP address of your DNS server there. If you don’t have a local DNS server, leave this line commented out.
- NOTE: If you don’t have a local DNS server configured, OpenVPN will default to using Google’s public DNS records. This means that you won’t be able to access any of your local network resources by hostname, only IP address. If you’d like to configure a local DNS server, you can check out my tutorial on Pi-hole here.
- NOTE: This is a very basic example of how DNS can be used.
- client-cert-not-required: This option is not added by default but should be added if you will be using the new OpenVPN clients (most people will be). If you don’t add this option, you will receive an error message when you connect. While you can proceed through the error message, this will stop the error from occurring.
dev tun tls-client remote YOUR_SERVER_IP 1194 # The "float" tells OpenVPN to accept authenticated packets from any address, # not only the address which was specified in the --remote option. # This is useful when you are connecting to a peer which holds a dynamic address # such as a dial-in user or DHCP client. # (Please refer to the manual of OpenVPN for more information.) #float # If redirect-gateway is enabled, the client will redirect it's # default network gateway through the VPN. # It means the VPN connection will firstly connect to the VPN Server # and then to the internet. # (Please refer to the manual of OpenVPN for more information.) #redirect-gateway def1 #redirect-gateway ipv6 #REQUIRED for iOS 7 and above. # dhcp-option DNS: To set primary domain name server address. # Repeat this option to set secondary DNS server addresses. #dhcp-option DNS DNS_IP_ADDRESS pull # If you want to connect by Server's IPv6 address, you should use # "proto udp6" in UDP mode or "proto tcp6-client" in TCP mode proto udp script-security 2 comp-lzo reneg-sec 0 cipher AES-256-CBC auth SHA512 auth-user-pass client-cert-not-required -----BEGIN CERTIFICATE----- [YOUR CERTIFICATE WILL BE HERE. LEAVE THIS ALL AS DEFAULT] -----END CERTIFICATE-----
- Save the configuration file and add it to any devices that you’d like to test the VPN connection with. I normally test the connection with my cellphone, as you cannot be on the same network as your VPN server. You MUST be testing this from an external network (cell phone/hotspot is a great option).
Step 5: OpenVPN Client Configuration and Testing
Now that we have configured everything, we need to test our connection. Download the OpenVPN client on your cell phone or on a PC that you can connect to a different network. Remember, you must be connected to a different network to test this.
- Download the OpenVPN client software for your device here.
- Select the add button at the bottom and then choose File. You should now be prompted to browse for the .ovpn file that we created earlier. Upload the file and then login with your DSM username and password.
- You should be able to connect to your VPN now.
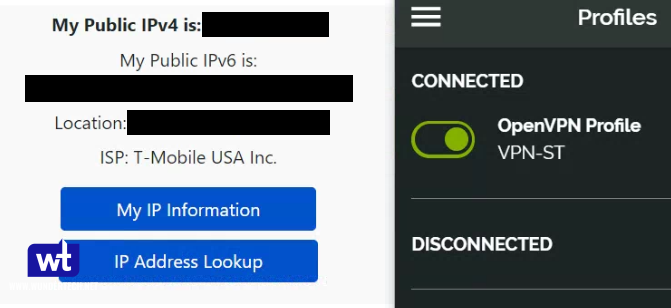
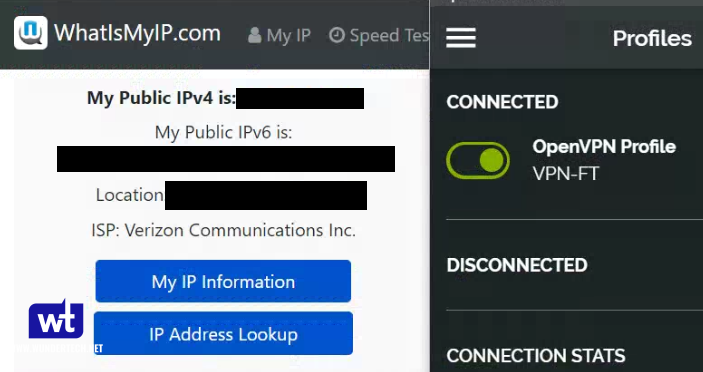
- I am going to show two examples below. First, I am connected to my VPN Server using my split tunnel connection. You can see that my external IP address is my mobile network (as I am accessing an external webpage).
- In this screenshot, I am connected to my VPN Server using my full-tunnel connection. My external IP address is my ISP’s, as all traffic is being routed through my home network.
Both, split tunnel and full tunnel VPN connections allow you to access your local resources, but full tunnel VPN connections should be used if you’re trying to secure your network traffic (like when you’re on public Wi-Fi).
Step 6: Static Route Configuration
This step is not required unless you need to access VPN devices from your home network.
Your home network and VPN network will be on different subnets which means that your local devices will only be able to talk to the machines on its subnet (VPN network will see both).
In order to have your local network talk to your VPN network (in my case, 192.168.1.X and 10.5.0.X), a static route will need to be configured in your router. I cannot go over the setup steps for this as each router is different, but below is a screenshot of the static route that I configured.
The Gateway IP Address will be the IP address of your Synology NAS (since that’s where your VPN is running). The 10.5.0.0/24 subnet is where you will need to enter the IP range you are using (as defined in the OpenVPN settings).
Conclusion & Final Thoughts
This tutorial looked at how to set up OpenVPN on a Synology NAS. Configuring Synology’s VPN Server allows you to securely connect to your home network to access your NAS and local resources.
It also completely bypasses the need for QuickConnect or exposing your NAS to the internet (which is a security risk). As an added benefit, the full tunnel VPN connection will also secure your connection when on public Wi-Fi devices!
There’s one thing that I want to mention in regard to the security of this VPN. Synology does a pretty poor job of letting the user configure this as securely as possible. With the way that this is configured, technically, you are exposed to a man-in-the-middle attack.
There’s a lot that has to happen in order for you to be exposed to that type of attack, but I want to mention that it is a valid concern. If complete security is your top concern, I would look into implementing OpenVPN on a Raspberry Pi or your router (if applicable).
The device running OpenVPN doesn’t really matter, it just needs to be able to easily configure the server/client certificates.
Thanks for checking out the tutorial! If you have any questions on how to set up OpenVPN on a Synology NAS, please leave them in the comments!
by Elena Constantinescu
Elena started writing professionally in 2010 and hasn’t stopped exploring the tech world since. With a firm grasp of software reviewing and content editing, she is always trying… read more
Updated on
- If you have a Synology NAS device, you can turn it into a VPN server to allow other users to connect remotely and share files securely.
- It’s a time-consuming process, but it’s not difficult if you accurately follow our complete step-by-step guide.
- The biggest decision is choosing the VPN protocol for the Synology NAS server: PPTP, L2TP/IPsec, or OpenVPN.
- We’re showing you exactly how to configure Synology VPN settings and how to connect.
A NAS is a data storage server that you can connect to your home or office network.
You can use it to save all essential data in a single place, including photos and videos, without having to rely on cloud storage.
Anyone can access these files through the Internet using a web browser or mobile app: you, your family, or your team members.
If you have a Synology NAS, it means that you can turn it into a VPN server on your Windows 10 PC.
This way, users can remotely connect to the NAS device and perform file transfers, safe from hacker interceptions.
Check out our complete step-by-step guide below to find out how to easily set up and connect to Synology VPN on Windows 10.
Before getting started
When setting up the Synology VPN server, you have to choose a VPN protocol from PPTP, L2TP/IPsec, and OpenVPN.
Keep in mind that the VPN clients must apply identical configurations to their devices in order to establish a successful connection.
Furthermore, any modifications made to the VPN configuration must be also updated in the VPN clients.
How we test, review and rate?
We have worked for the past 6 months on building a new review system on how we produce content. Using it, we have subsequently redone most of our articles to provide actual hands-on expertise on the guides we made.
For more details you can read how we test, review, and rate at WindowsReport.
That means you should take into account the devices and operating systems used by the VPN clients.
At the same time, you need to ensure anti-hacker VPN protection, so you can’t set the bar low for security.
Which VPN protocol should I use?

Most platforms and operating systems have native support for PPTP, so it’s really easy to set it up without installing additional software.
However, PPTP has weak security and is mostly considered obsolete because of this. Also, some old routers block the GRE protocol (IP protocol 47), which is required for VPN connections over PPTP.
L2TP/IPsec provides better security than PPTP and has good compatibility with most devices, including Windows, Mac, Linux, and mobile.
It requires DSM 4.3 or newer. If you make any changes to the L2TP/IPsec VPN server, this can be easily applied at the VPN clients, too.
OpenVPN offers the best security among the three, but it’s not built into operating systems. That means that VPN users must install an OpenVPN client (free to use).
On top of that, you need to export the OpenVPN configuration every time you make changes and share it with the VPN clients. Plus, OpenVPN server mode doesn’t support bridge mode for site-to-site connections.
We suggest using OpenVPN for best security or L2TP/IPsec for good security and native integration.
How do I set up a Synology NAS VPN server on Windows 10?
For PPTP
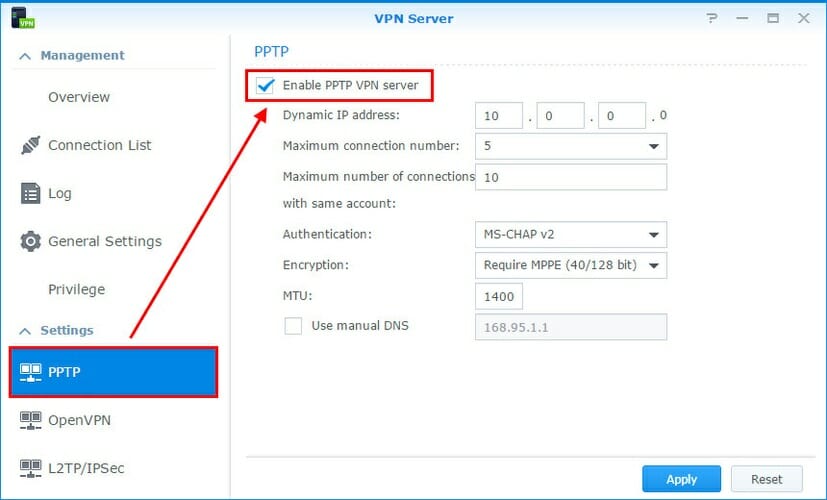
- Click VPN Server on your Synology NAS
- Select PPTP on the left side
- Check the Enable PPTP VPN server box
- Set the Dynamic IP address*
- At Maximum connection number, you can limit the number of simultaneous VPN client connections
- The Maximum number of connections with same account field is similar to the one before, but it refers to users logged in under the same VPN account
- Set Authentication to MS-CHAP v2 to encrypt the VPN client passwords
- Set Encryption to Require MPPE
- Leave MTU to default (1400)
- Leave Use manual DNS unchecked to push the Synology NAS DNS server to the VPN clients
- Click Apply
For L2TP/IPsec
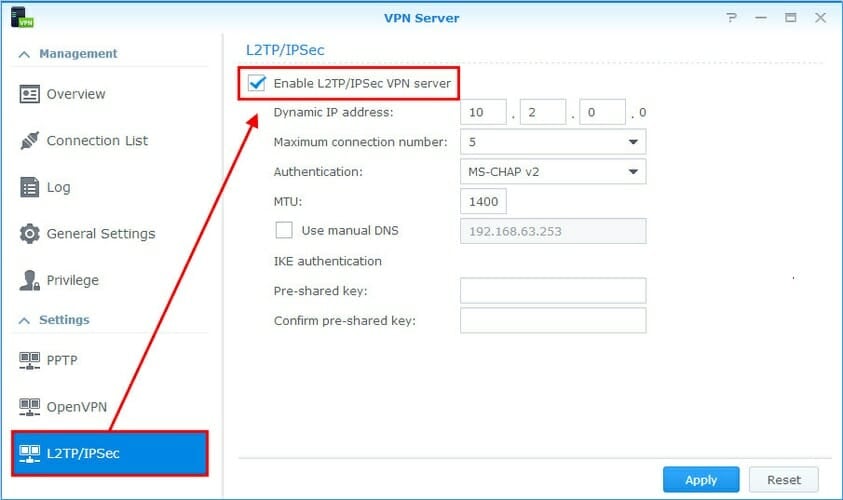
- Open VPN Server and go to L2TP/IPsec on the left side
- Check the Enable L2TP/IPsec VPN server box
- Enter the Dynamic IP address*
- Set Maximum connection number to the total simultaneous VPN client connections you allow
- Set Authentication to MS-CHAP v2
- Leave MTU to default (1400)
- Leave Use manual DNS unchecked to push the Synology NAS DNS server to the VPN clients
- At IKE authentication, enter and confirm the pre-shared key.
- Click Apply
For OpenVPN
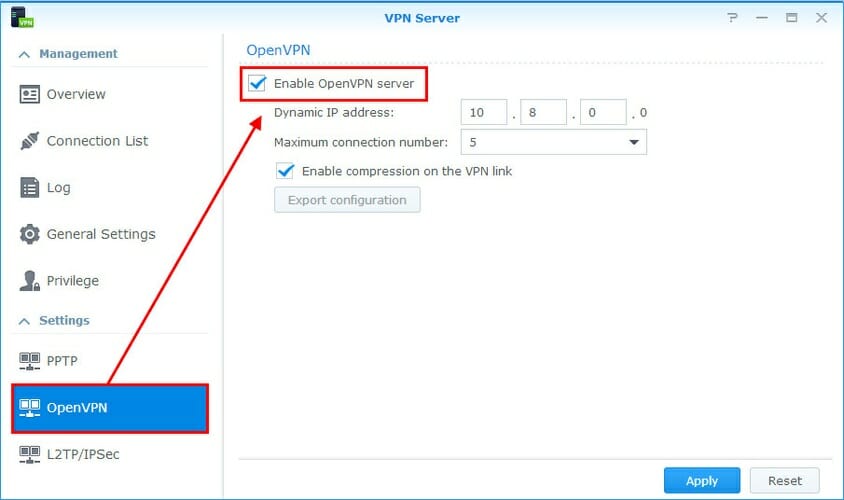
- Launch VPN Server and select OpenVPN on the left side
- Check the Enable OpenVPN server
- Set the Dynamic IP address*
- Limit the Maximum connection number
- At Enable compression on the VPN link
- Tick it if you want to apply data compression and speed up file transfers
- Leave it unchecked if you don’t want it to consume additional system resources (lower speed).
- Enable Allow clients to access server’s LAN
- Tick Enable IPv6 server mode only if you want VPN clients to connect using IPv6 instead of IPv4
- Click Apply
*The dynamic IP address is taken into account by the VPN server when it assigns the virtual IP addresses to all connected clients. It should not be identical to any local IP addresses used by your devices in LAN. You can use the arp -a command in CMD to view all local IP addresses.
Many routers have VPN server support for PPTP and L2TP/IPsec.
To avoid conflicts caused by occupied ports, make sure that the VPN server isn’t enabled on your router if you want to set up a Synology VPN server over PPTP or L2TP/IPsec.
Furthermore, you should use a router that allows VPN pass-through.
How do I connect to Synology VPN on Windows 10?
For PPTP
Here’s how to add a VPN connection, edit VPN properties, and connect to the Synology VPN when using the PPTP protocol.
For L2TP/IPsec
When it comes to the L2TP/IPsec protocol, start by making a minor registry tweak
Then, you can add your VPN connection, edit L2TP/IPsec settings, and connect to the Synology VPN.
For OpenVPN
The OpenVPN option is the most complicated because you have to install an OpenVPN client (no operating system has native support for OpenVPN).
Before doing that, you have to get the OpenVPN configuration settings ready. Once everything is set up, you can connect to the Synology OpenVPN server.
- Prepare the OpenVPN configuration
- On the Synology VPN server, select OpenVPN from the left side
- Click Export configuration
- Copy the ZIP archive to the VPN client PC
- Unzip the archive and open the openvpn.ovpn file with any text editor
- Replace YOUR_SERVER_IP with the public IP address of the Synology NAS
- Set up the OpenVPN client
- Download OpenVPN GUI and install it on your PC
- Go to the config subfolder of the OpenVPN directory. The default location is:
C:Program FilesOpenVPNconfig - Copy the Synology OpenVPN configuration files (ca.crt and openvpn.ovpn) to this location
- Connect to the OpenVPN server
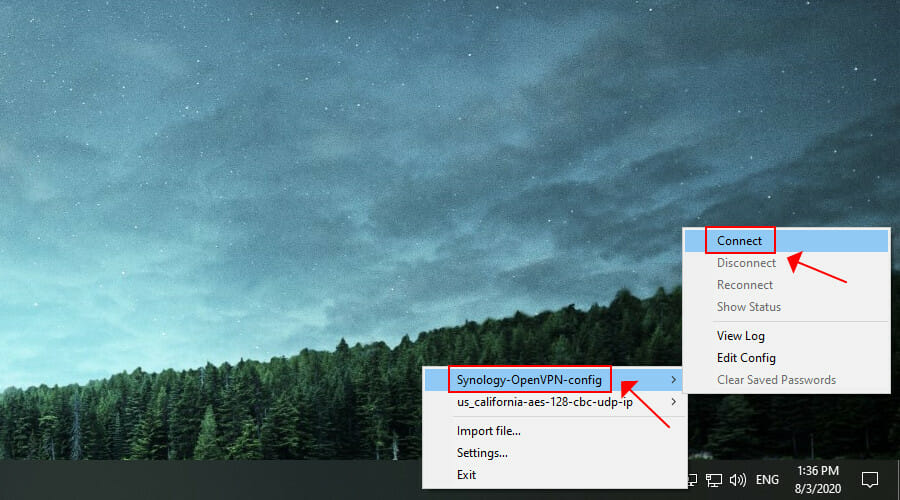
- Launch OpenVPN GUI as admin
- Right-click the OpenVPN GUI icon in the systray
- Select the Synology OpenVPN profile and click Connect
Synology VPN troubleshooting
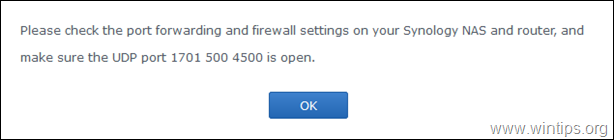
To avoid VPN connection issues, it’s a good idea to check port forwarding and if the required ports are opened in the firewall on the Synology NAS and router, for both the VPN server and clients.
- PPTP requires port 1723 over TCP
- L2TP/IPsec needs ports 1701, 500, and 4500 over UDP
- OpenVPN needs port 1194 over UDP
Conclusion
To sum up, you can turn your Synology NAS into a VPN server and then connect to it from any part of the world to access files.
It’s a time-consuming process, but it’s not difficult at all if you follow the instructions accurately.
You just need to set up the right VPN protocol for your home or office. No matter what you choose, you can change the VPN settings anytime to try something else.
,
In this tutorial you will find step-by-step instructions on how to set up Synology NAS as an L2TP VPN server and how to connect to it and access its files over the Internet. Configuring your Synology NAS as a VPN server will allow you to remotely and securely access the shared files on your Synology NAS Server, and the Synology NAS Server’s internal network, protecting you from Internet attacks and data interception.
How to Set up & Connect to Synology NAS L2TP VPN Server.
Part 1. Setup L2TP VPN Server on Synology NAS.
Part 2. Setup a VPN Client for Synology NAS VPN Server.
Part 1. How to Setup & Configure Synology NAS as a VPN Server.
Step 1. Install and Enable VPN L2TP Server on Synology NAS.
1. Go to Packages and install the VPN Server package
2. Open VPN Server Package.
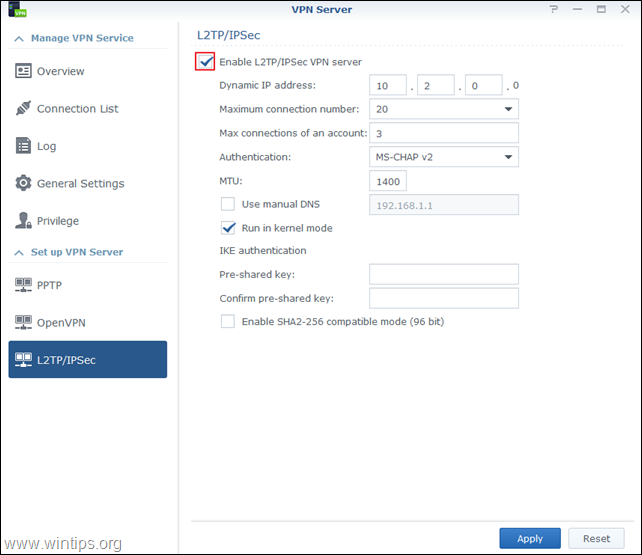
3. Navigate to L2TP/IPSec and select Enable L2TP/IPSec VPN Server.
4. Specify a virtual IP address of VPN server in the Dynamic IP address fields, or leave the default. *
* Notes:
1. The Dynamic IP Address specified here, will be the Virtual IP address of the VPN server.
2. The Dynamic IP addresses allowed for VPN server can be any of the following:
- From «10.0.0.0» to «10.255.255.0»
- From «172.16.0.0» to «172.31.255.0»
- From «192.168.0.0» to «192.168.255.0»
5. Set Maximum connection number to limit the number of concurrent VPN connections.
6. Set Maximum number of connections with same account to limit the number of concurrent VPN connections with the same account.
7. Select the MS-CHAP v2 authentication method, in order the VPN clients passwords to be encrypted during authentication.
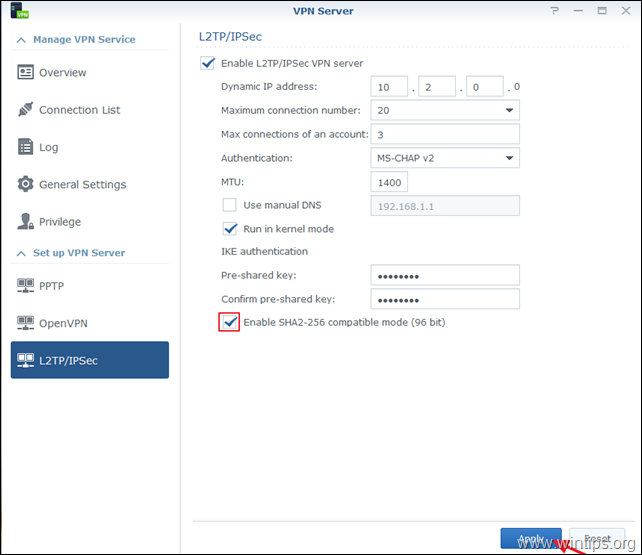
8. Click at Pre-shared key box and select Use a Securely Generated Password, or specify your own strong key/password. (don’t forget to write the key down).
9. Check the Enable SHA2-256 compatible mode (96 bit) to permit certain clients (non RFC standard) to use L2TP/IPSec connection.
10. When done, click Apply.
11. Finally, click OK at message informing you which ports needed to open in you Firewall in order the L2TP VPN Server to work.
Step 2. Setup PORT Forwarding Rules for Synology VPN Server on your Router/Firewall.
The next step is configure the L2PT/IPSec port forwarding to your router.
1. Login to router’s web interface.
2. Inside the Router configuration setup, forward the following ports to the IP address of the Synology VPN Server: 1701, 500 & 4500 (UDP)
Part 2. How to Connect to Synology VPN Server from Windows 10.
Step 1. Allow L2TP Connections Behind NAT in Registry.
By default, modern Windows 10, 8 or 7 and the Windows Server 2016, 2012 & 2008 operating systems do not support L2TP/IPsec connections if the Windows computer or the VPN server are located behind a NAT. To bypass this problem you have to modify registry as follows, on the Windows VPN client/computer:
1. Open Registry Editor. To do that:
1. Simultaneously press the Win
+ R keys to open the run command box.
2. Type regedit and press Enter to open Registry Editor.
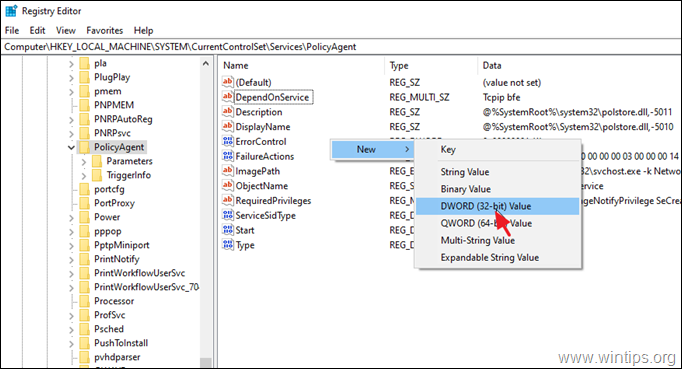
2. At the left pane, navigate to this key:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Sevices\PolicyAgent
3. Right click at an empty space at the right pane and select New –> DWORD (32 bit) Value.
4. For the new key name type: AssumeUDPEncapsulationContextOnSendRule and press Enter.
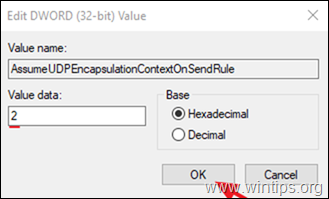
* Note: The value must be entered as shown above and with no space.
5. Double click at AssumeUDPEncapsulationContextOnSendRule value, type 2 at Value data and click OK.
6. Close Registry Editor and reboot the machine.
Step 2. Configure a new VPN L2TP Connection for Synology VPN Server on Windows 10.
Upon making the required modification in Registry, you’re ready to create and setup the VPN connection to the Synology NAS L2TP VPN server.
1. From Settings click Network and Internet, OR, right click at the Network icon on the taskbar and choose Open Network & Internet settings.
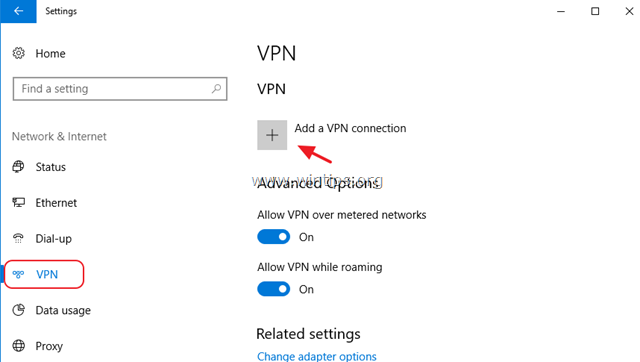
2. Click VPN on the left and then click + to Add a VPN connection.
3. At the next screen, fill out the following information and click Save:
- VPN provider: Windows (built-in).
- Connection name: Type a friendly name for the VPN connection. (e.g.. «Synology VPN»)
- Server name or address: Type the public IP address or the DNS Name of the VPN server (e.g. «example.dyndns.net» .
- VPN Type: Use the drop down arrow and select L2TP/IPsec with pre-shared key.
- Pre-shared key: Type the Pre-shared key.
- Type of sign-in info: Use the drop down arrow and select User name and password.
- User Name: Type your VPN User name.
- Password: Type your VPN Password.
- Check the «Remember my sign-in info» checkbox, if you want to save your sign-in credentials for the VPN connection and then click Save.
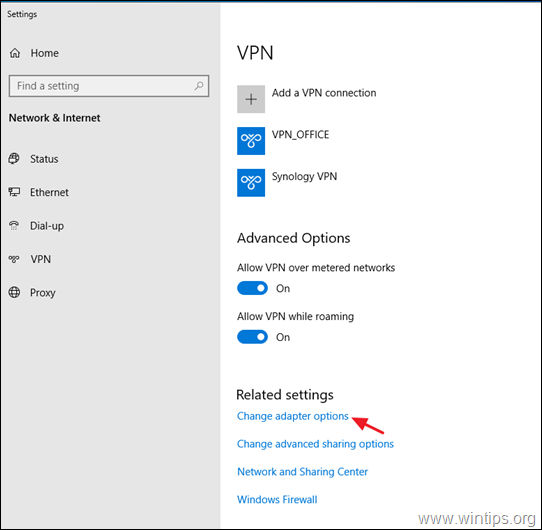
4. Now click Change adapter options.
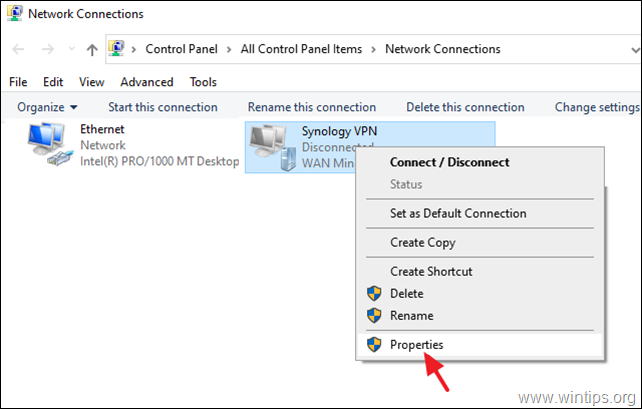
5. Right-click on the VPN Connection for the Synology NAS an select Properties.
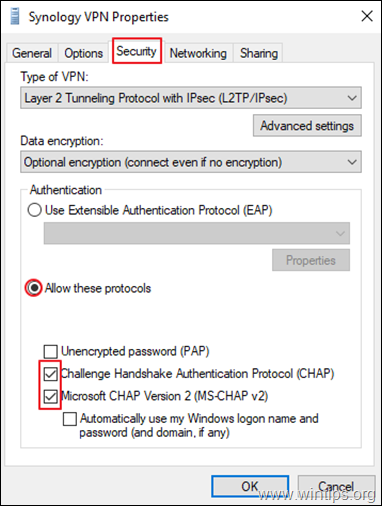
5a. At Security tab, select Allow these protocols, and check the following protocols:
- Challenge Handshake Authentication Protocol (CHAP)
- Microsoft CHAP Version 2 (MS-SHAP v2)
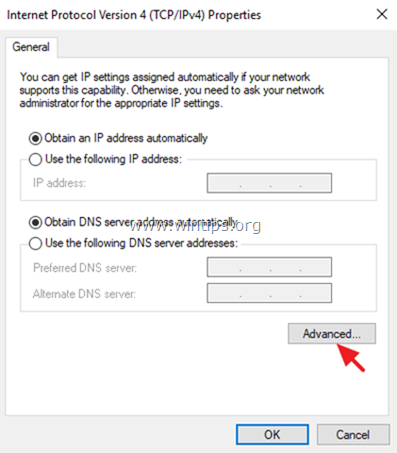
5b. At Networking tab:
- Uncheck the Internet Protocol Version 6 (TCP/IPv6).
- Select the Internet Protocol Version 4 (TCP/IPv4) and click Properties.
5c. Click Advanced.
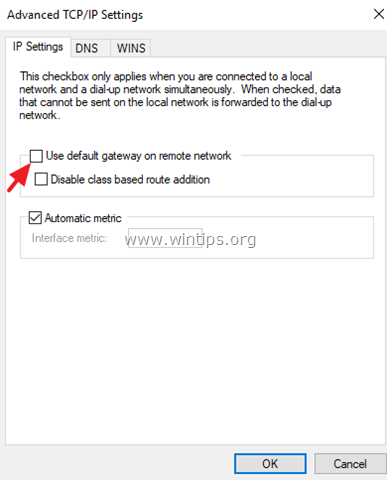
5d. Uncheck the «Use default gateway on remote network«* and click OK three (3) times to apply changes and close all windows. *
Note: By keeping this setting enabled, all the Internet traffic of the client computer, will pass through the VPN’s Server network, so its better to keep this setting disabled. BUT, proceed and enable this setting only if you cannot access other devices on Synology NAS network.
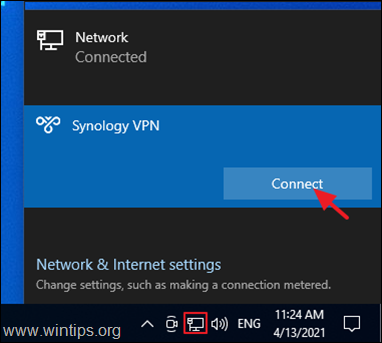
6. Finally, click on Network icon on the taskbar, select the Synology VPN network connection and click Connect to connect to your Synology NAS VPN Server.
7. If the connection is successful, proceed to check if you can access the shared files on your NAS Server. (see step-3 below)
Step 3. Access NAS File shares.
Now check if you can access the file shares on your Synology NAS Server, by doing the following:
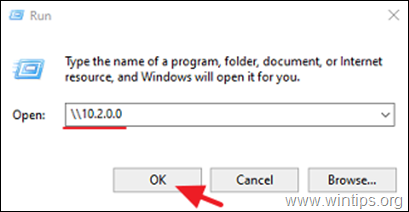
1. Simultaneously press the Win + R keys to open the run command box.
2. Type «\\» followed by the Virtual IP address of the VPN server (e.g. «\\10.2.0.0» in this example), and click OK.
3. If you can access the file shares on your Synology NAS server, then you ‘re done.
That’s it! Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:

- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).
Using VPN with Synology NAS teaches you to set up a VPN connection between a VPN client and a Synology NAS that hosts a VPN server. This instruction focuses on a VPN connection based on the OpenVPN standard and this standard combines a good level of security with ease of installation.
Table Of Contents
- Using VPN with Synology NAS
- Process Overview
- Prepare Your Network And NAS
- Secure your Synology NAS
- Fixate internal IP address
- Discover external IP address
- Forward port on the router
- Enable DDNS On NAS
- VPN Server On NAS
- Install the VPN Server package
- Configure VPN Server certificate
- Configure the VPN Server
- Configure the firewall
- Configure VPN Server backup
- VPN Client On Computer Or Mobile
- Editing the VPN configuration
- Installing and configuring the VPN Client
- Using the VPN connection
- Monitor Your Connections
- Monitor the VPN server
- Monitor the VPN Connect client
- Troubleshoot your connection
- Thanks for reading
Compared to other remote access solutions like DDNS or reverse proxy, a VPN or Virtual Private Network takes an entirely different approach to overcome the challenges of accessing your internal network over the internet.
As the name suggests, you create a private network virtually over the internet. The VPN connection you make is between your computer’s VPN client and your internal network’s VPN server, while encryption secures the connection between the endpoints.
For connecting over the internet, a VPN connection is considered more secure compared to the DDNS/port forwarding way because:
- the listening port is password protected
- all traffic to and from the private network is encrypted
Another benefit of a VPN connection is accessing your DiskStation as if you are on the internal network.
Despite the benefits of a VPN, it may be complex to set up and troubleshoot. A VPN is not for the faint of heart, it seems. Hopefully, this post helps more users overcome to achieve their goal of a safe remote connection.
Note that there are other options where the VPN server in the network runs in a Docker container on your NAS or the internet router.
These options have advantages, but it makes the installation more complex. This post covers the VPN Server application as part of DSM.
For a quick overview of the Synology VPN Server application, please reference the VPN Server datasheet.
Process Overview
Before we start clicking on buttons, I outline using a VPN with Synology NAS.
First, you make some preparations on your network and NAS. Next, you install the VPN server, export the VPN connection details in a configuration file, and edit the configuration.
Moving over from the VPN server to your computer, you download and install the VPN client and apply the configuration file. And last but not least, you test your connection.
If the connection fails, you will find some troubleshooting tips.
Prepare Your Network And NAS
Before installing Synology’s VPN Server package on your NAS, there are some preparations to make.
Secure your Synology NAS
The moment that you decide to connect your NAS to the internet, in whatever way, you should take any possible measure to prevent unwanted access to your device. And in case this happens, you should have your recovery plan ready.
Securing your NAS starts with a solid backup and recovery strategy, a password policy, 2-factor authentication, disabling SSH, and enabling notifications, among others. Please refer to my post Secure your Synology NAS [sorry, in preparation].
Fixate internal IP address
Before installing a VPN service, you must ensure that the NAS always has the same IP address on your local network because your internet router will redirect incoming VPN traffic to a specific IP address.
In general, IP addresses are dynamic on your local network, which is usually fine. But in this instance, you must fixate on the address.
Please see my post How To Configure A Fixed IP Address, for details on achieving this goal.
Discover external IP address
Your internet router is the linking pin between your internal network and the internet or external network. On both sides, the router has an IP address.
Knowledge of the external or internet-facing address of the VPN server location is essential because that is where the VPN client on your computer has to go to.
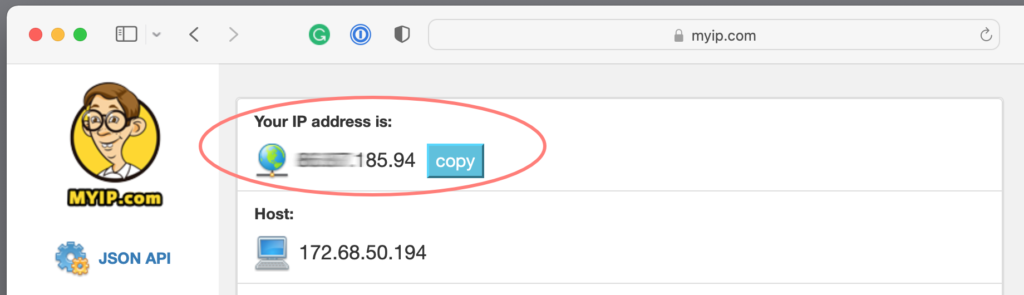
To discover the external IP address of the location where you create the VPN server, open your browser and point it to https://myip.com. Copy your IP address from the top of the page and save it in a note for later reference unless you use DDNS.
If your external IP address is dynamic, it can change over time, as with most consumer connections, you need DDNS. I discuss enabling DDNS below. If you have a static IP address, skip the section on DDNS and keep the external IP address for reference later.
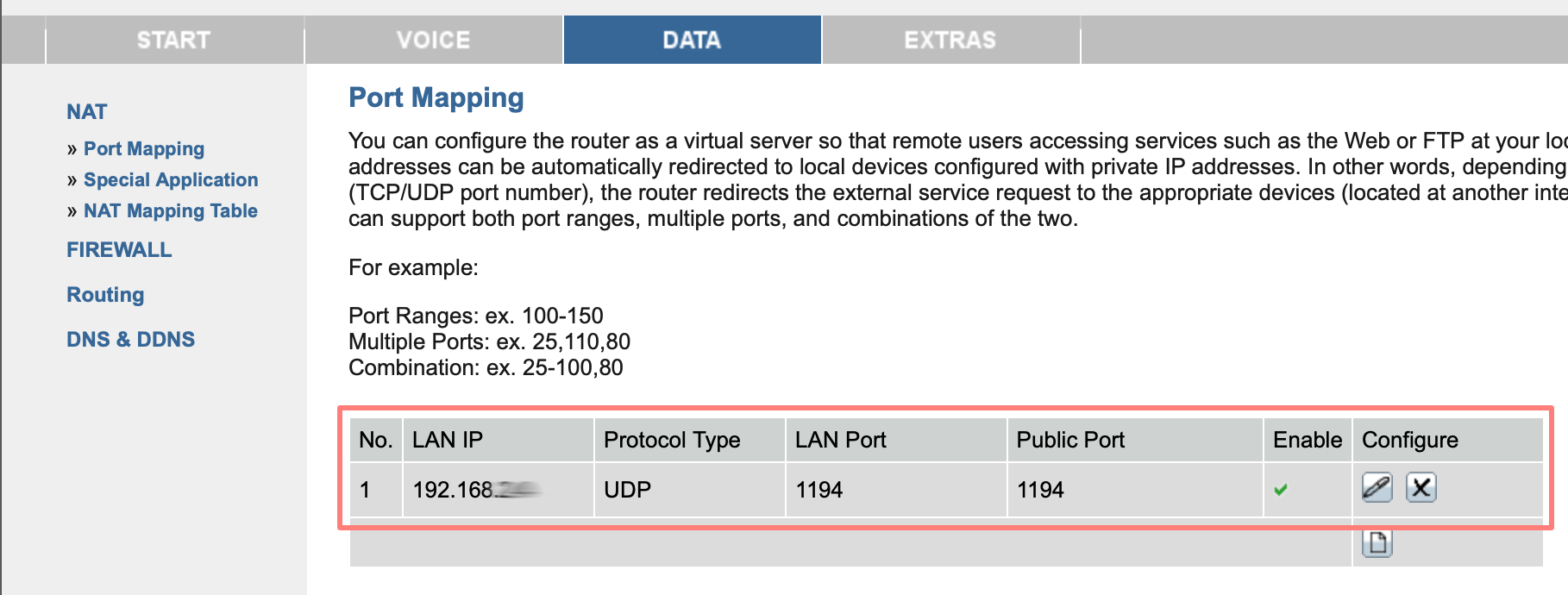
Forward port on the router
Port forwarding is a very crucial step in the process. Once the VPN client on your computer goes out to connect, it looks for your internet router. The router listens at a specific port and forwards traffic coming in on that port to the NAS. Now, you have to instruct your router to do precisely that.
Unfortunately, there are countless routers, and they are all different. You can do an internet search for a manual for your brand and model. Generic steps are:
- While on the network where the NAS is, open your browser and type in your router’s IP address. This is primarily the default gateway and log in.
- look for a port forwarding tab; it is often part of features like IP, network, NAT, or firewall
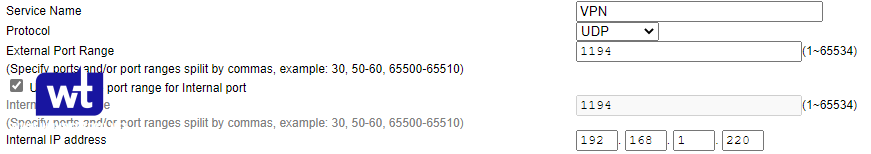
- enter UDP port 1194 and forward the port to the IP address of your NAS
- save your settings
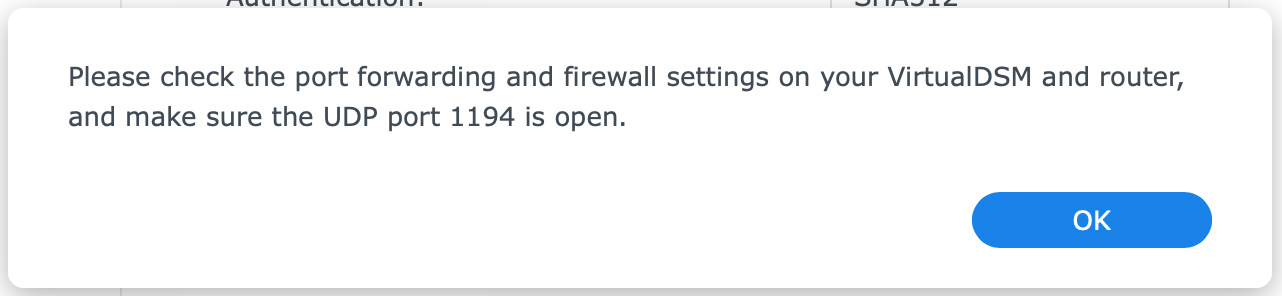
You must forward UDP port 1194 to the same port on your NAS for OpenVPN. Fill in the IP address of your NAS that you made static earlier.
Enable DDNS On NAS
Most of us do not have a fixed external IP address. If we use the current IP address in the VPN configuration of the VPN client, chances are that you will not be able to connect at one moment in the future.
We enable DDNS or Dynamic DNS on the NAS and use it as an in-between to resolve this issue. DDNS registers your current external IP address to a name. If your IP address changes, it automatically records the new address to that name. The DNS name of DDNS remains the same.
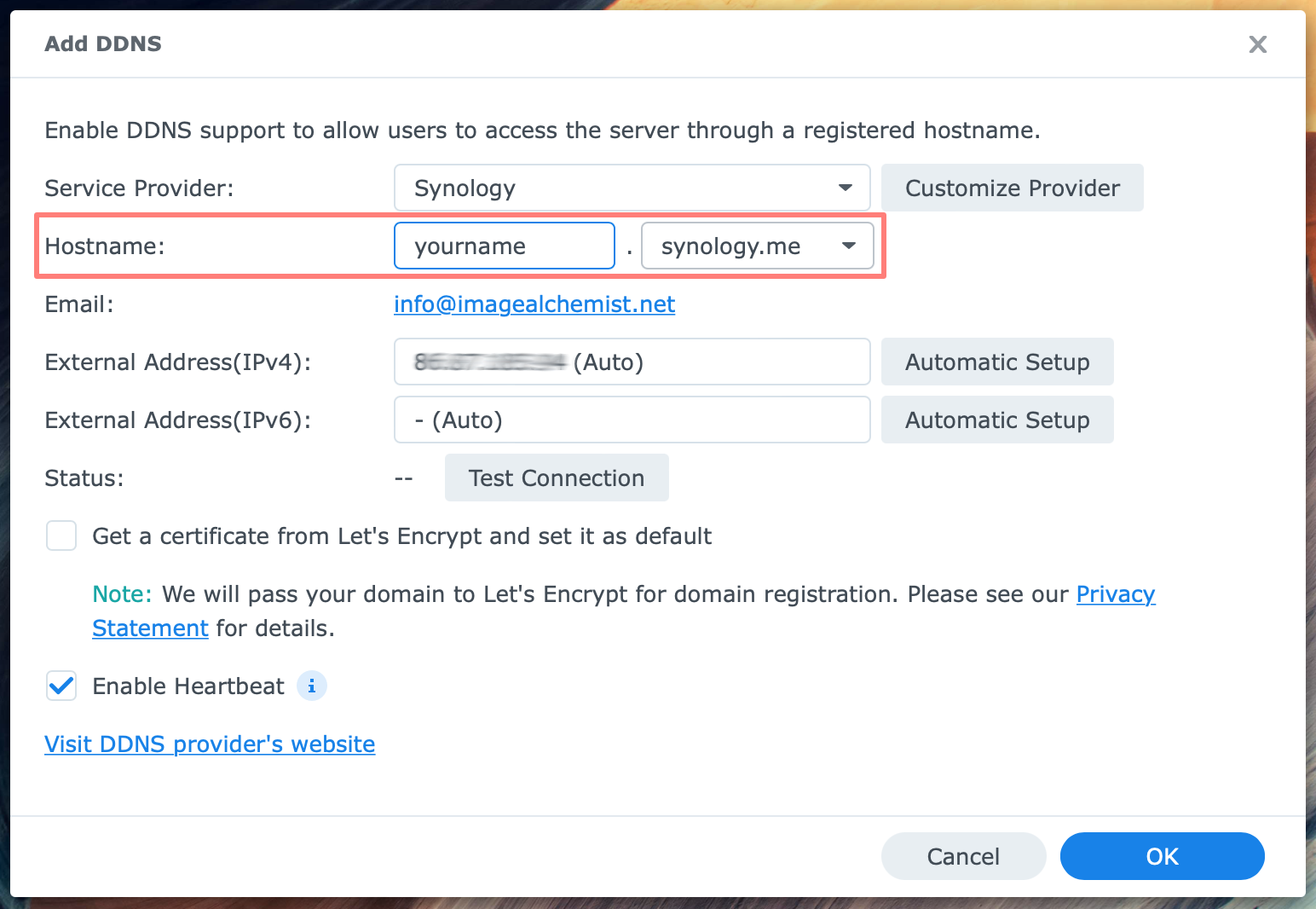
Log in to DSM with an administrator account. Open Control Panel, External Access under Connectivity. In the pane at the right, select the DDNS tab. Click on the Add button. The DDNS page (DSM 6) or Add DDNS page (DSM 7) opens.
On the Add DDNS page, select a Service Provider. I choose Synology, listed at the top, but you can choose a different provider.
Under Hostname, enter a hostname. As an example, I filled in yourname. Please fill in your hostname.
The synology.me domain is automatically added because you chose Synology as the service provider in the previous field. Notice that the full name will become yourname.synology.me.
Under Email, either the email address of your Synology account appears or you are requested to sign in.
Notice that under External IP address (IPv4), you can also find your external IP address.
You do not have to request a certificate from Let’s Encrypt because you do not use DDNS to connect to the NAS. We use a VPN for that. Keep the heartbeat enabled. It is a bonus feature.
Click OK to save the configuration and wait a few seconds for the DDNS connection to appear on the DDNS page.
VPN Server On NAS
After the preparations outlined above, you can set up the VPN Server application and service and start using VPN with your Synology NAS.
Install the VPN Server package
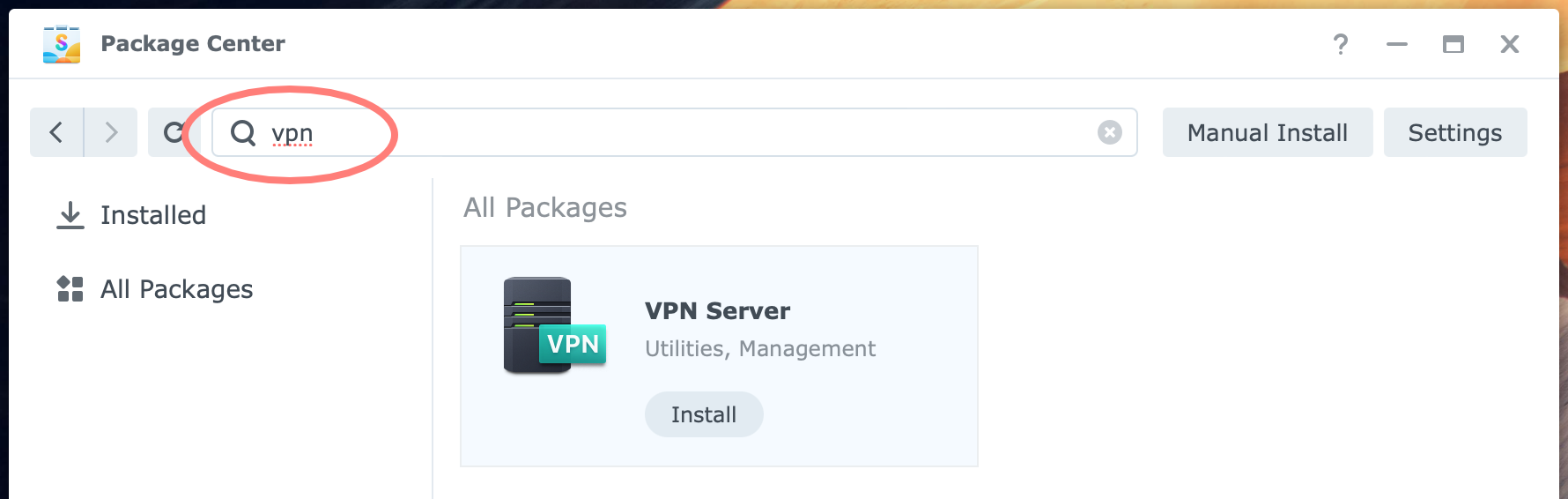
Log in to the DSM desktop with an administrator account and open Package Center.
In the search bar at the top, search for VPN. On the VPN Server package, click Install. The VPN Server – Install wizard starts.
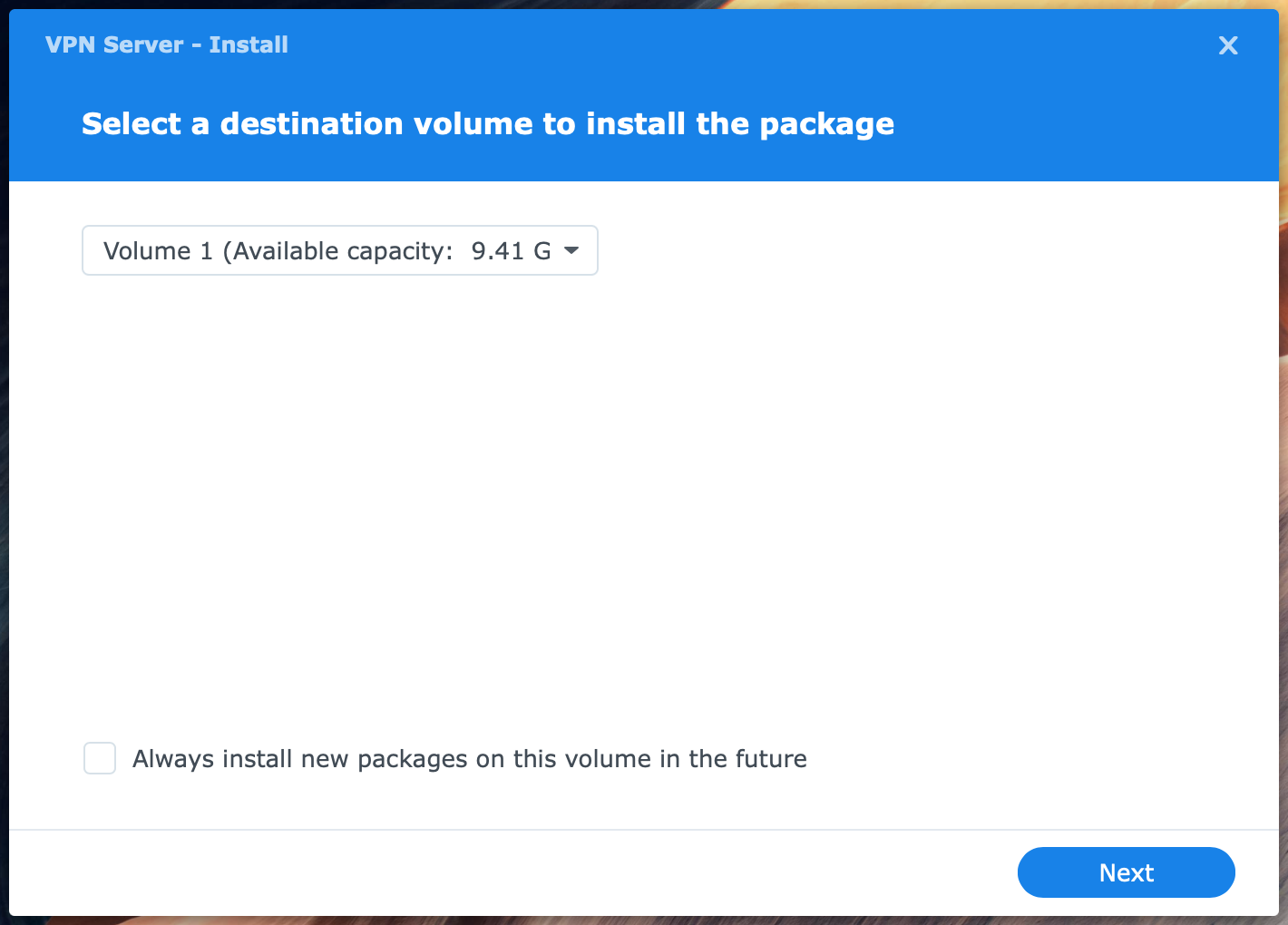
You can select a volume to install the VPN Server on the first screen. Note that this screen does not appear if you have a single volume in your NAS. Click Next.
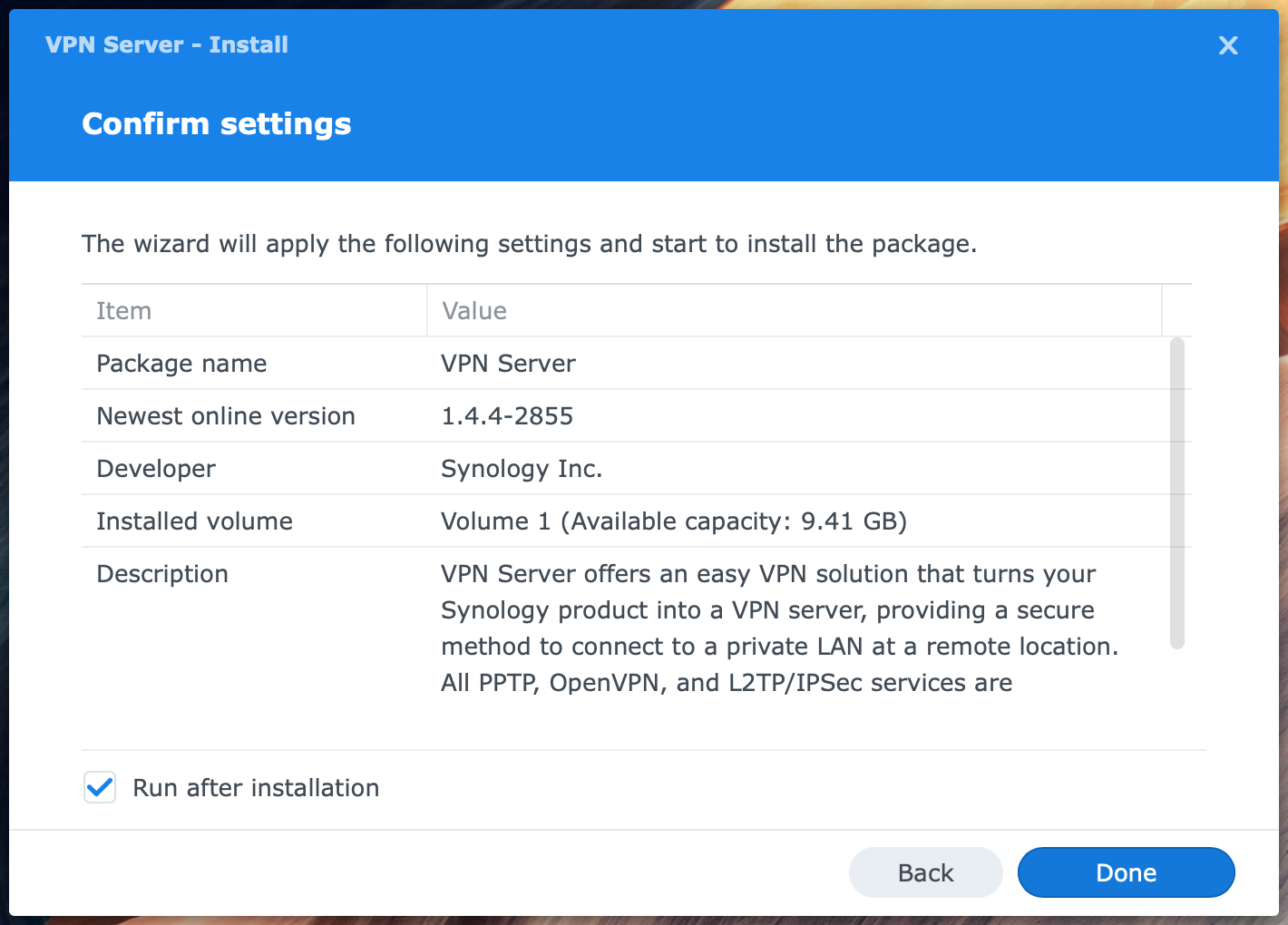
Ensure that the Run after installation box is checked and click Done.
You return to Package Center, and you can follow the progress of the installation. When the installation finishes, select the Open button. Note that you can open VPN Server from the main menu in the top-left corner of the screen.
You can now close Package Center.
Configure VPN Server certificate
You installed the VPN Server package. The next step is a formality, perhaps, but necessary anyway. DSM assigns a certificate to the VPN Server. We are going to check on that.
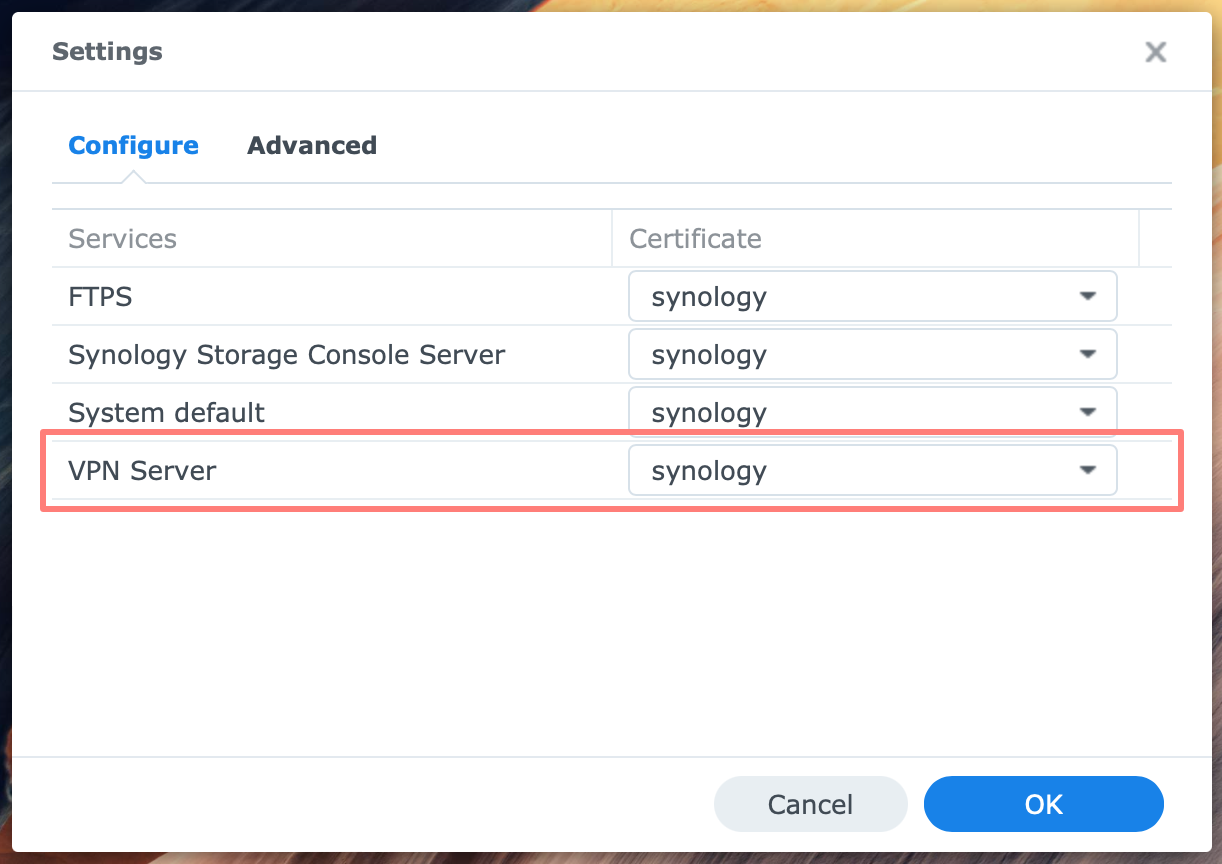
Go to Control Panel > Security > Certificate and click on the Configure (DSM 6) or Settings (DSM 7) button.
In the list of Services, look for the VPN Server and the certificate assigned to it. If this is the correct certificate, you like to use for the service, close Control Panel and continue.
If it is not the proper certificate, click on the drop-down list next to the VPN Server and select the appropriate certificate.
There is no right or wrong certificate. The VPN Server uses the certificate in the .ovpn configuration file for the VPN client. This file contains the certificate for the connection and must match the certificate in Control Panel. Therefore, be aware that when you change the certificate for the VPN Server in Control Panel, all VPN clients that use a configuration made with the previous certificate will fail to connect.
Renewal of a current (read: not expired) Let’s Encrypt certificate had no adverse effect on connecting with an older configuration. Renewal renews the expiration date but does not change the certificate’s contents.
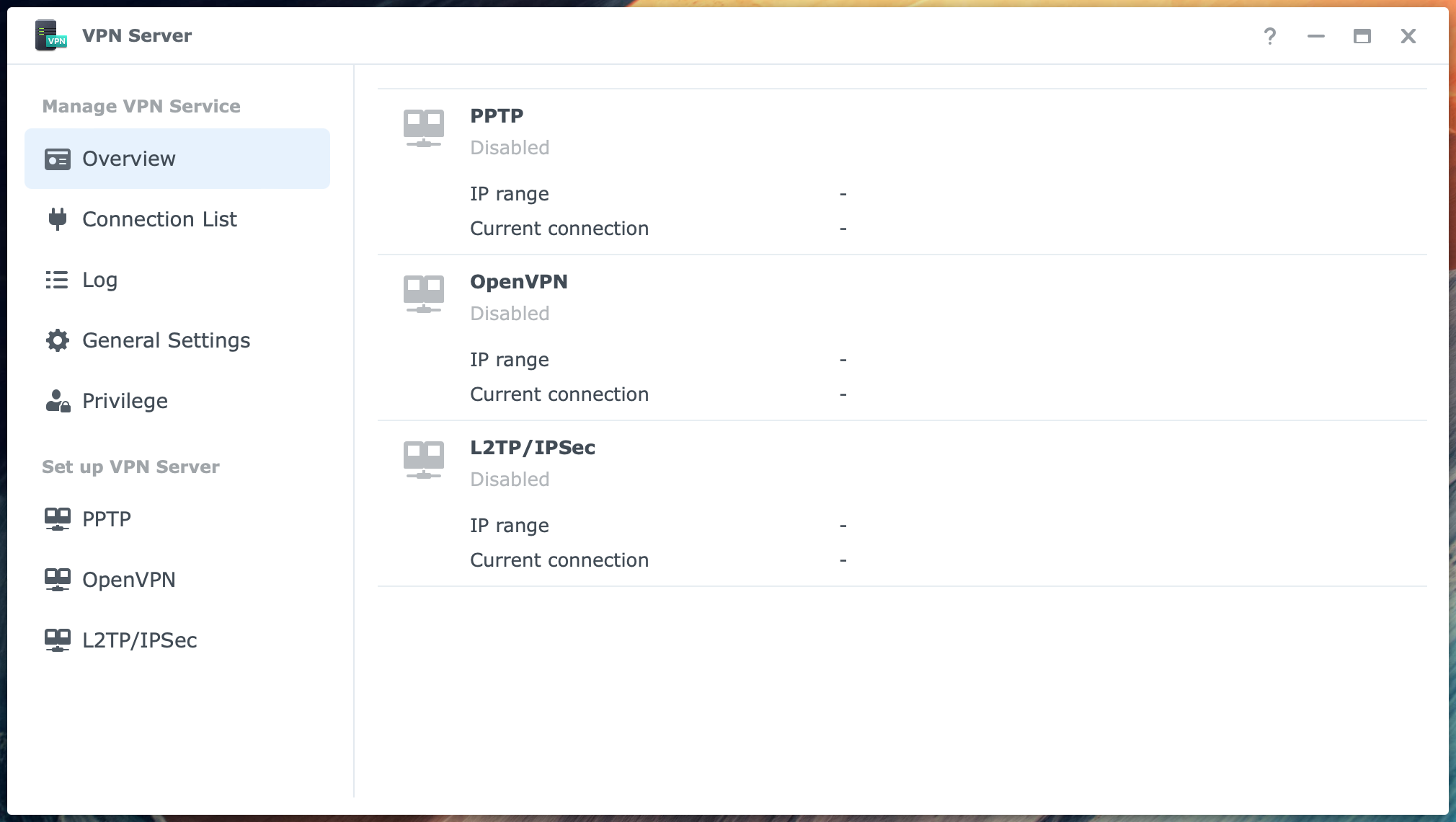
Configure the VPN Server
You first see the Overview page when you open the VPN Server application. Notice that there are three protocols, PPTP, OpenVPN, and L2TP/IPSec. They are all disabled at this stage, but that will change.
In the column at the left, you can select different items grouped under Manage VPN Service and Set up VPN Server.
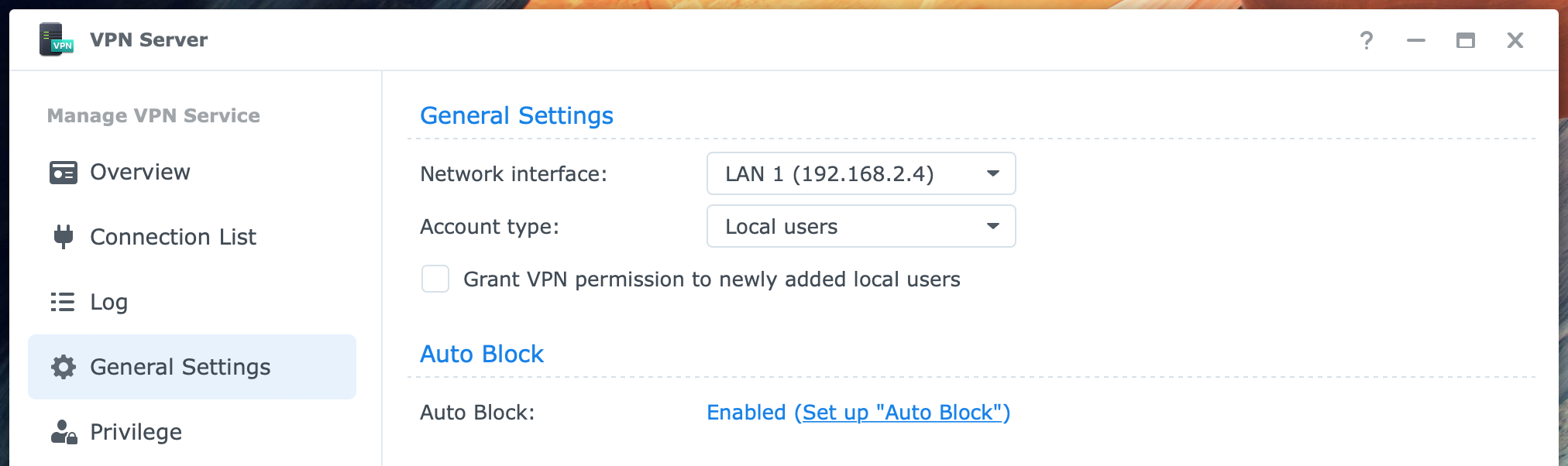
In the left column, our first stop is General Settings. The Network interface setting is only relevant when you have multiple network interfaces. Select the interface connected to the internet router that receives the incoming VPN connections.
You can grant the VPN permission to new users that you add in the future. This prevents you from separately enabling them on the Privilege page. But perhaps you like to only give selected users explicit permission. If so, uncheck this box.
Auto Block should be enabled in Control Panel. This is part of securing your NAS that I mentioned at the beginning of this tutorial.
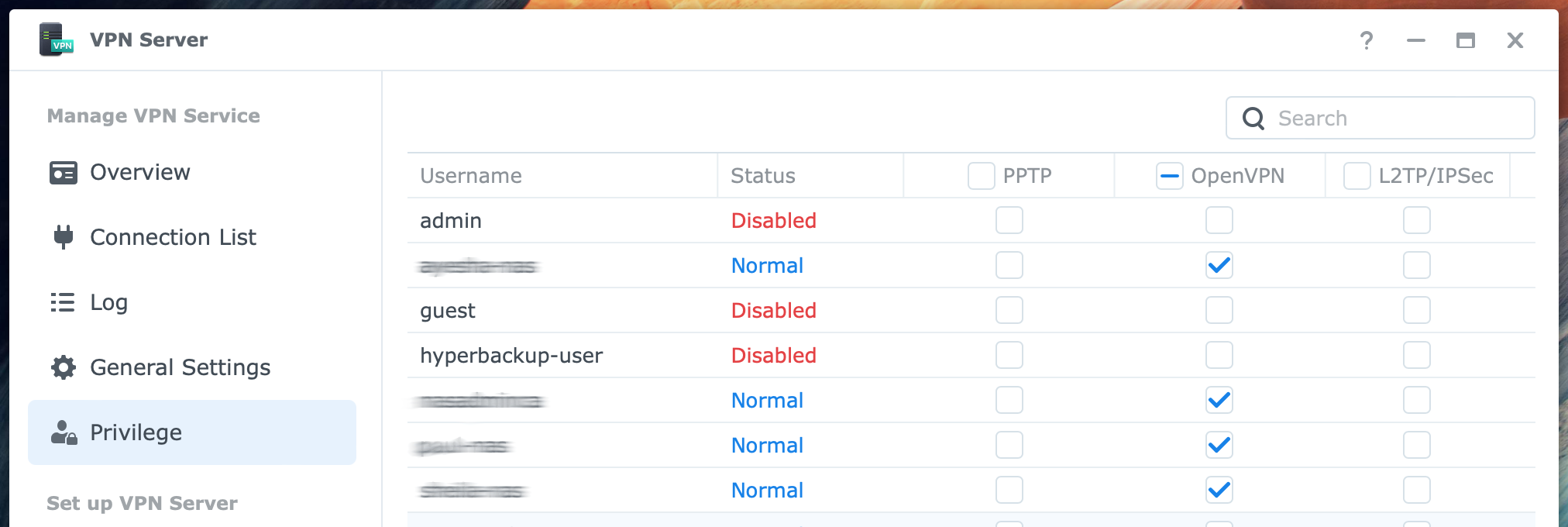
In the left column, select Privilege under Manage VPN Service. On the Privilege page at the right, you see the user accounts and three columns for the respective VPN protocols. You enable those who can use the VPN service on a per-user and per-protocol basis. Set a checkmark for the users you want to grant VPN access to.
Uncheck both PPTP and L2TP/IPSec unless you use either of these protocols in addition to OpenVPN.
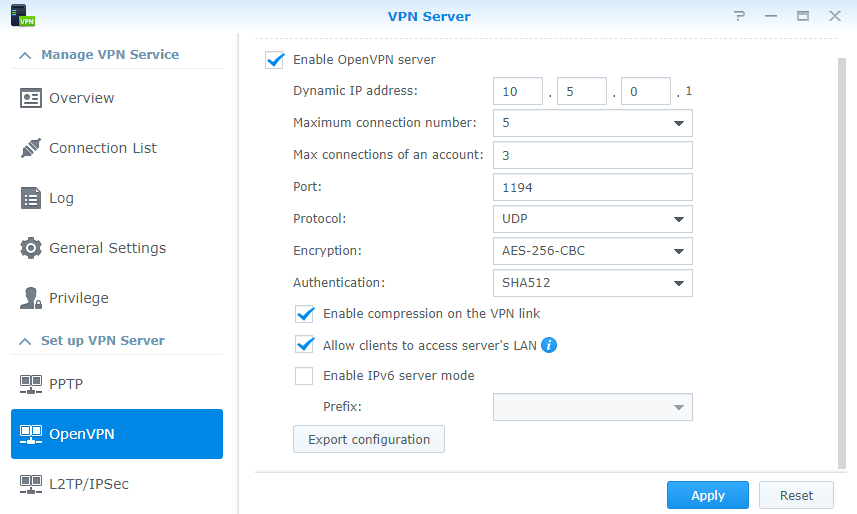
In the left column, select the option OpenVPN below Set up VPN Server.
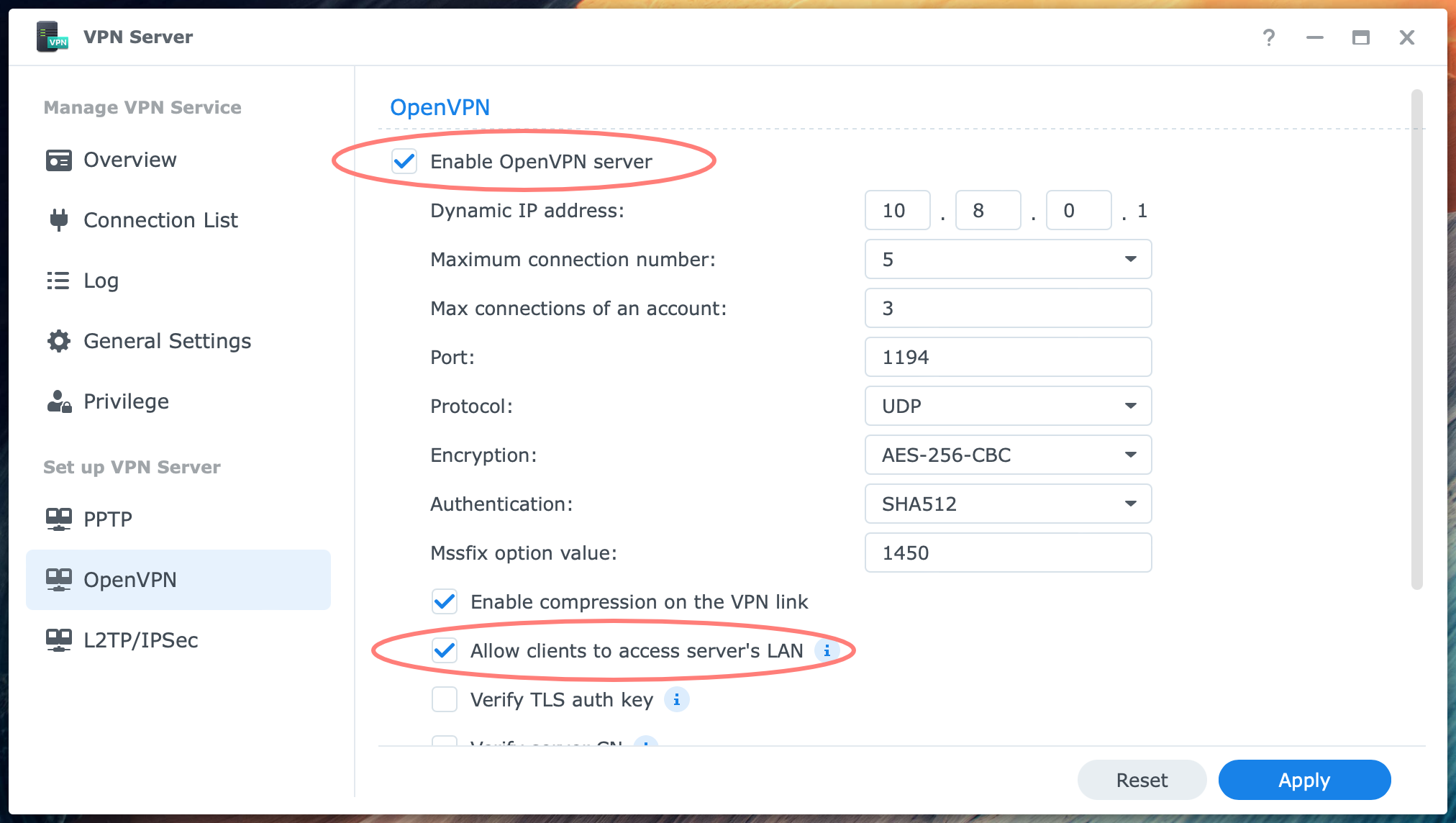
Check the box Enable OpenVPN server at the top of the OpenVPN screen. There are several predefined settings, and you can leave it as is in most cases.
Review the settings and, in particular, the Dynamic IP address 10.8.0.1 at the top. In general, this is good and needs no change. However, if your local network, where the NAS with the VPN Server resides, happens to have a network segment in the 10.8.0.0 range; you do need to change this. In other words, the VPN server must have an address in a different range than your local network. Click the Apply button.
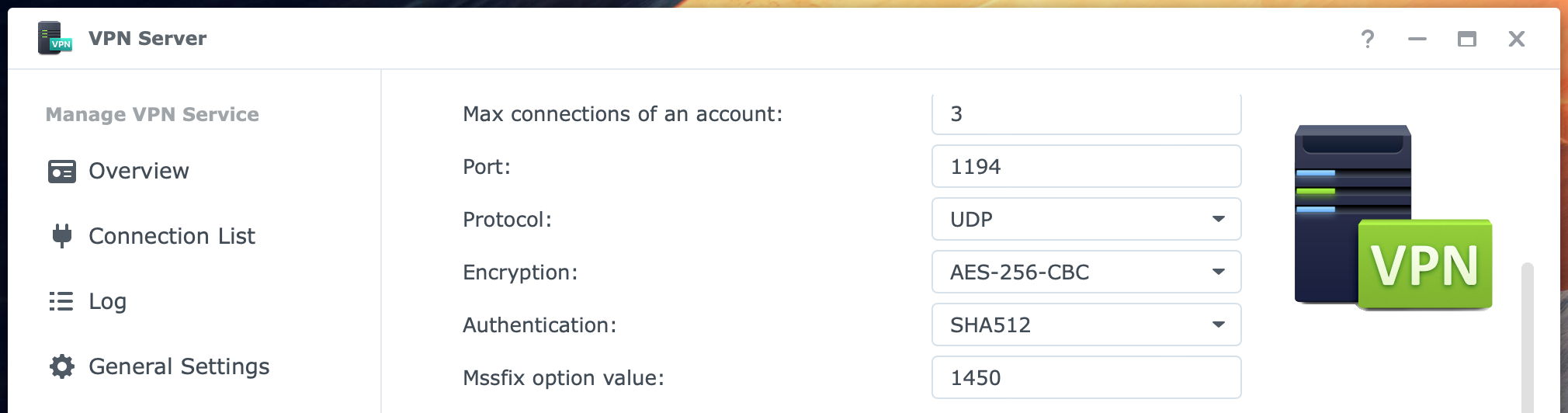
The Maximum connection number default is 5, the lowest value. When you expect more simultaneous users, raise the amount. The Maximum connections of an account default are 3. You could lower it if you see a reason for it. The port and protocol are 1194 and UDP. I suggest that you only change the port if you insist on not having the default port number or if you have more than one OpenVPN server on the network. In that case, you need a different port for at least one of the VPN servers. The values for Encryption and Authentication are set very secure by default.
At the bottom of the page, there are five other checkboxes. Leave Enable compression on the VPN link checked, and enable Allow clients to access the server’s LAN. This last setting lets you go from the VPN server to the NAS on your network. If you have other devices like a second NAS, this will be accessible.
Notice the port forwarding and firewall warning for UDP port 1194. Click OK to close the message. See also my remark on the firewall below.
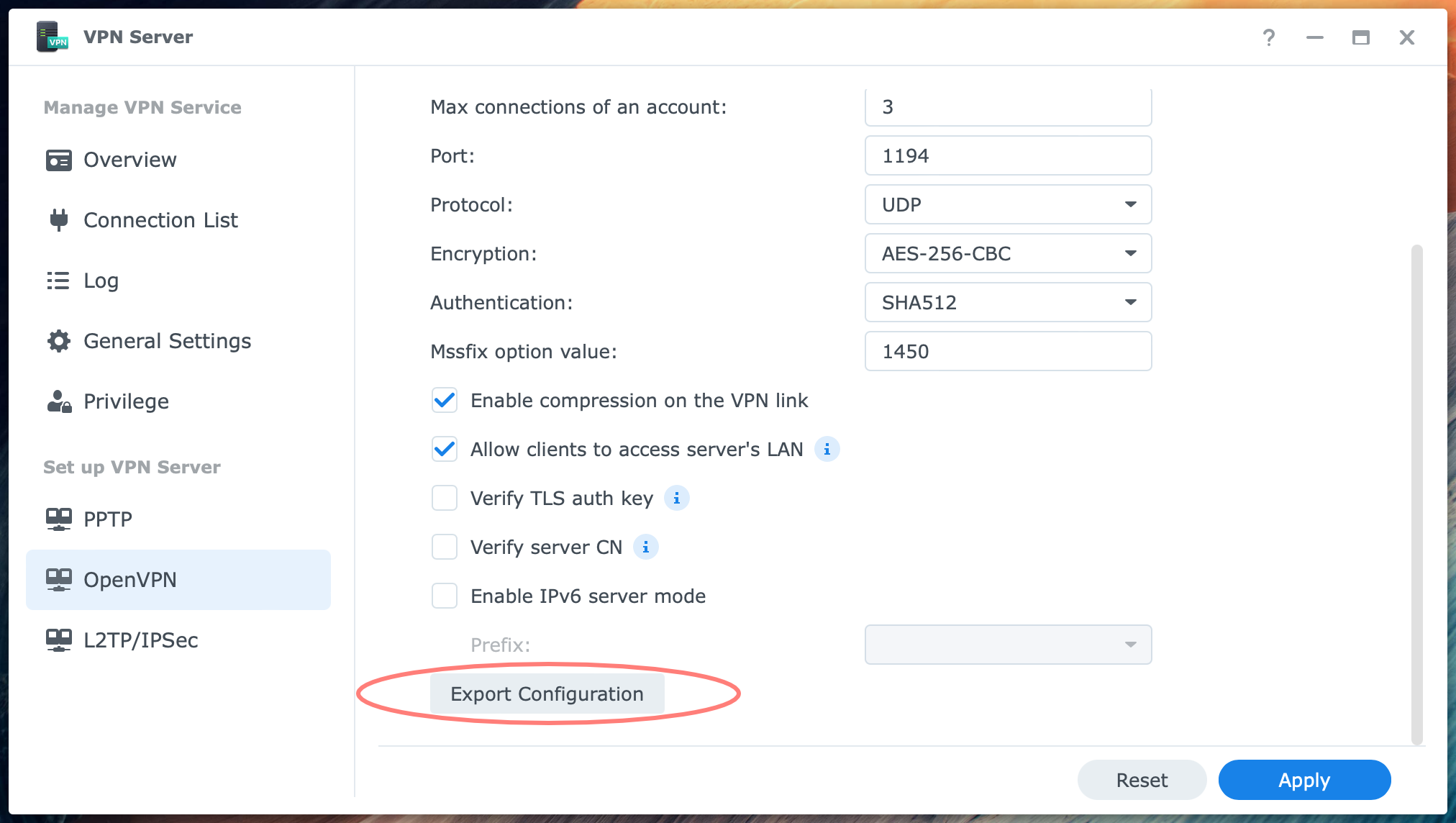
Notice that the Export Configuration button is available at the bottom of the OpenVPN screen of the VPN Server application. Click on the button to download the openvpn.zip file. We will configure its contents in a minute.
You can close the VPN Server application now.
Configure the firewall
I enabled the option “Allow clients to access servers’ LAN.” As the name suggests, I can access other hosts on the LAN via the VPN connection.
Strangely enough, with some of my clients, I can access other Synology NAS devices on the same LAN, but with some other clients, I can not. I can only access the NAS that runs the VPN Server.
I found out that when I allow the VPN Server’s subnet, typically 10.8.0.0/24 or 10.8.0.0 with subnet 255.255.255.0, in the firewall of the VPN Server’s NAS, the issue is resolved, and I can access other hosts on the local network.
To diagnose the problem, I used the ping command from a command box on the VPN client while connected. Without the rule mentioned, I could neither ping the VPN Server nor ping other hosts or access them.
Configure VPN Server backup
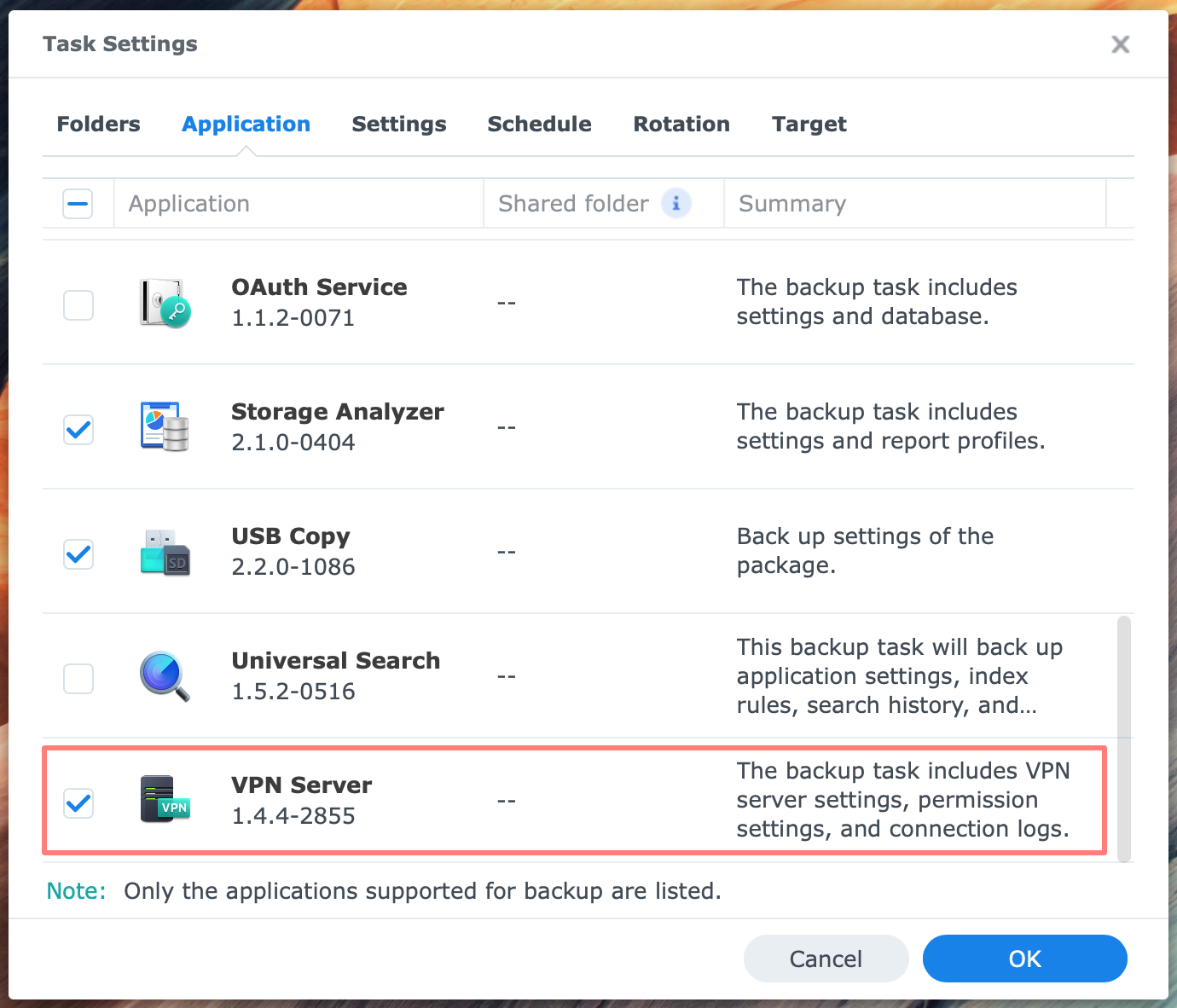
If you use Hyper Backup on your NAS, you can include the application settings in a data backup task.
From your DSM desktop, open Hyper Backup, select an existing data task, and click Edit. Go to the Applications tab, and check the box for VPN Server.
Click OK to save the task and close Hyper Backup.
VPN Client On Computer Or Mobile
You install a VPN client application on the computer, tablet, or smartphone, making a secure connection to the VPN server. Once the connection is established, you continue working as you would in the location where your NAS and VPN server reside.
You first edit the VPN configuration file you exported from the VPN server. Next, you install the VPN client and import the configuration. As you will see, I create a second profile for redundancy. Last but not least, you test the connection.
If the connection is unsuccessful, you will find some troubleshooting tips.
Editing the VPN configuration
In a previous step, you exported the configuration file. The export downloaded openvpn.zip to your computer. This zip archive contains two files, README.txt and VPNConfig.ovpn. Open VPNConfig.ovpn in a plain text editor like TextEdit or BBEdit on macOS or Notepad on Windows. Change the following line:
- remote YOUR_SERVER_IP 1194
Replace YOUR_SERVER_IP with the external IP address of your router. You can get your external IP address via https://www.myip.com, assuming you are at the location and network of the VPN Server.
Instead of the IP address, you can fill in the DDNS name if you configured that earlier. As you know, DDNS is preferred if you have a dynamic external IP address on your router.
- redirect-gateway def1
During the VPN connection, you create a virtual tunnel to your destination, where your NAS resides. However, you might want to access the internet for other tasks like web browsing or mail with an active VPN connection. The redirect-gateway def1 line affects how the VPN connection handles that internet traffic.
You create a so-called full-tunnel VPN when you enable the redirect-gateway def1 line by removing the # character. Internet traffic is direct via the tunnel to the VPN server’s location, typically your home or office. Next, from that trusted location, you browse the web.
This is a great configuration when you access the internet from an untrusted hotspot.
However, when you are at a trusted location, your home, for example, making a VPN to your office, you do not have to redirect other internet traffic through the VPN tunnel to the office. In that scenario, you leave the redirect-gateway def1 line marked out by the # character. This creates a so-called split-tunnel VPN. You access the internet for other non-VPN-related traffic directly from your current location.
Alternatively, you could make two configuration files, one disabled (trusted location, with #, known as split-tunnel VPN) and one enabled (untrusted location, without #, full-tunnel VPN).
- client-cert-not-required
Our configuration does not have a separate certificate file since the certificate is inside the configuration file. As a result, the VPN client generates a warning when we connect. To suppress that warning, add the client-cert-not-required statement at the end of the configuration lines.
Installing and configuring the VPN Client
Download the OpenVPN client from https://openvpn.net/vpn-client/. On macOS, it installs the OpenVPN Connect application in the Applications/OpenVPN Connect folder, including a shortcut. On Windows, it installs in the C:\Program Files\OpenVPN Connect folder and places a shortcut on the desktop.
Start the application.
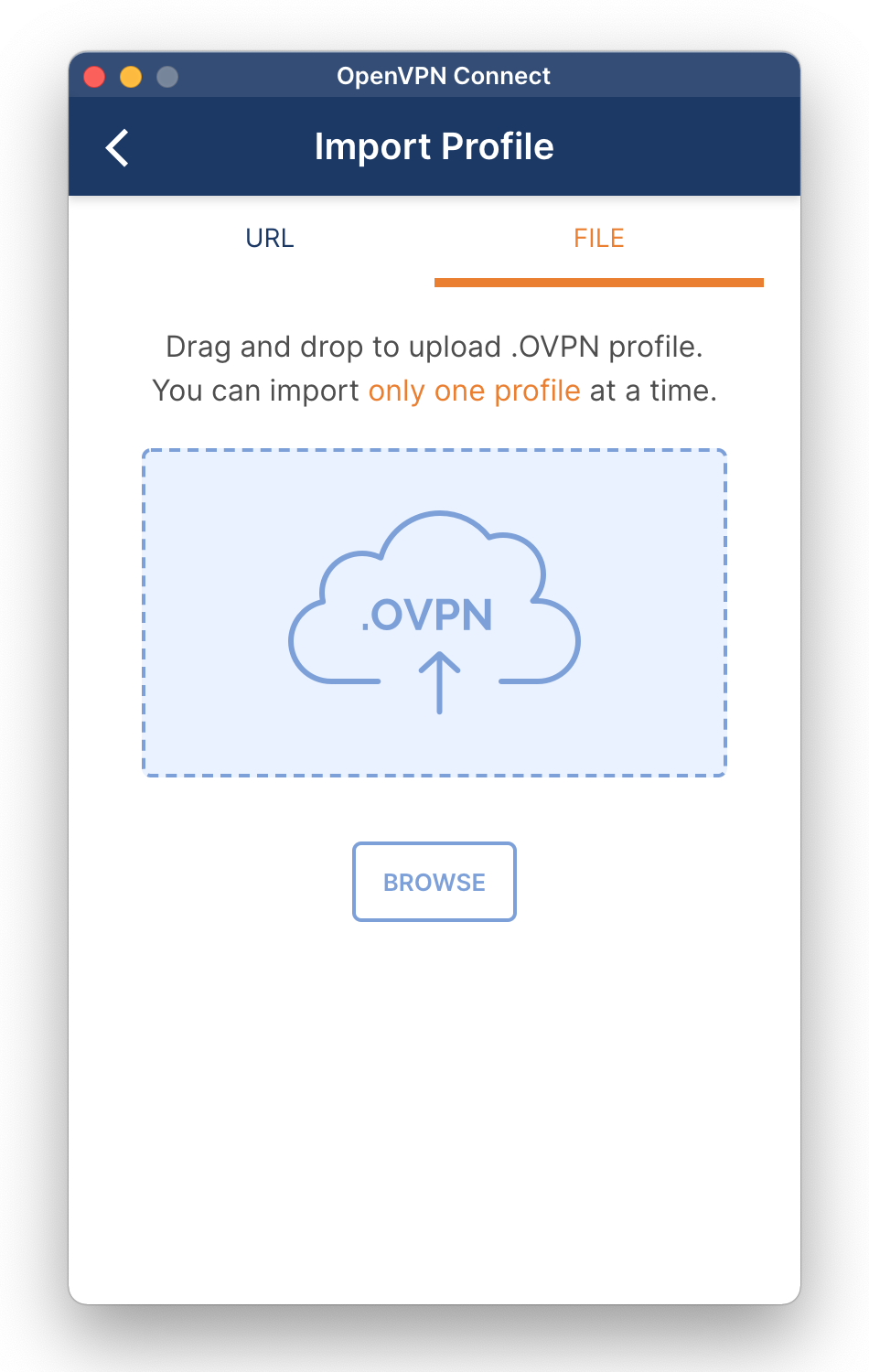
When you start the application for the first time, you get four screens with helpful information. On the last screen, click Get Started.
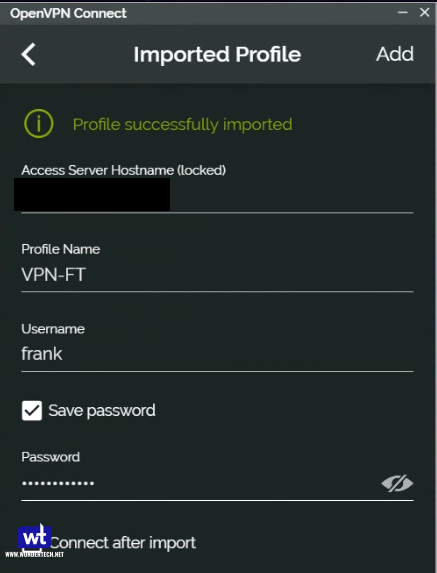
When you get the Import Profile screen, select the File tab, drag or import the .ovpn file you edited earlier, or use the Browse button. If you like to import another profile, click on the three bars in the top-left corner, and choose Import Profile.
Note that the application remembers the user name in the profile. The next time, you only have to enter the password. To change the user name, edit the profile.
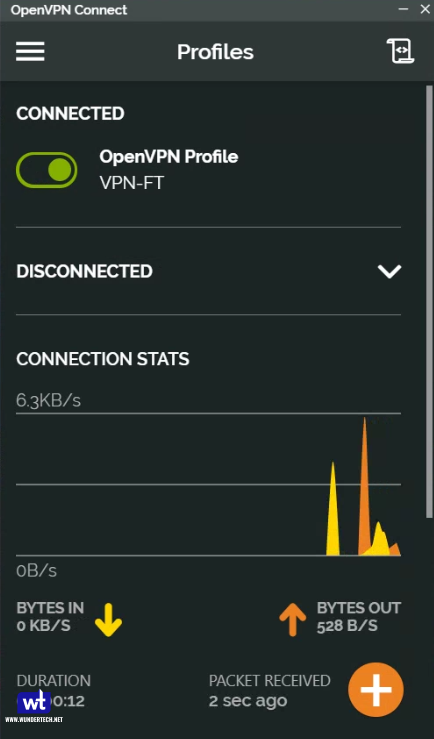
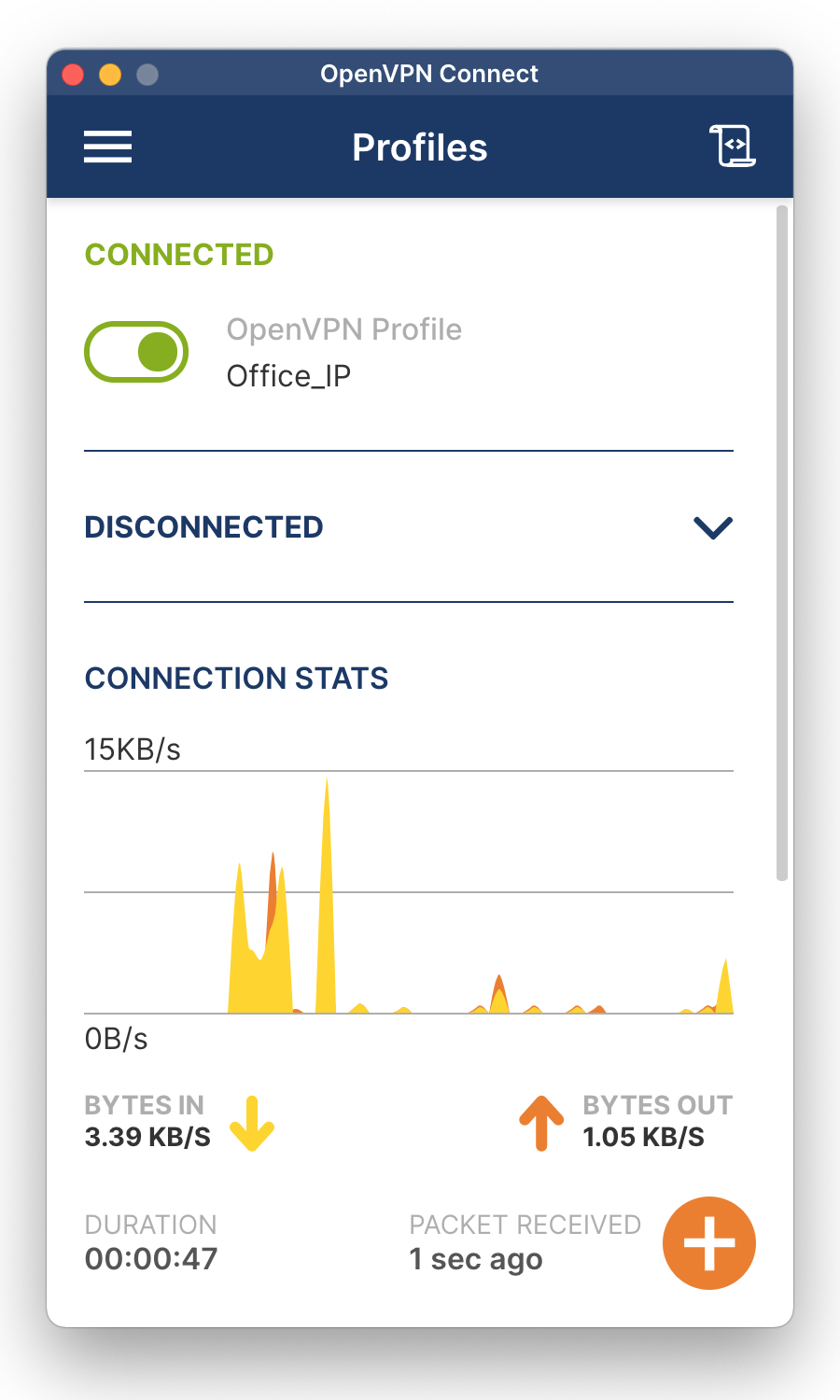
To connect, click on Connect. Enter the username and password of your user account on the NAS, and click OK.
When the message Connected in green appears, you are connected to the NAS by means of a VPN. Notice the connection statistics. You can disconnect by clicking the green button in the top-left corner and confirming the disconnect.
I have a remark for the safety-conscious among us. After importing the configuration file into the VPN profile, consider deleting the .ovpn file. You do not need them any longer, you can export them again if needed, and it contains security information (the password for the connection). Don’t have them laying around longer than necessary.
Using the VPN connection
Normally, when you connect to the NAS from the same network, without a VPN, you can use its name or IP address. But via a VPN connection, you can use the IP address only. There is a solution to circumvent this limitation by settings up a DNS server on the NAS or else in the network, but that is out of the scope of this tutorial.
Aliases and port numbers in the browser for applications on the NAS work via the VPN connection as they work from the local network.
Monitor Your Connections
The VPN server on your NAS and the VPN client keeps a log for monitoring and troubleshooting. Often you can test and connect with server and client on the same local network because many internet routers allow for loopback. But to insist on a full-proof test, either go to a different location and network or use your smartphone’s hotspot.
With your smartphone as a hotspot, you can connect any computer over WiFi via the smartphone to the internet.
Monitor the VPN server
As an administrator, log in to DSM and open the VPN Server application from the main menu.
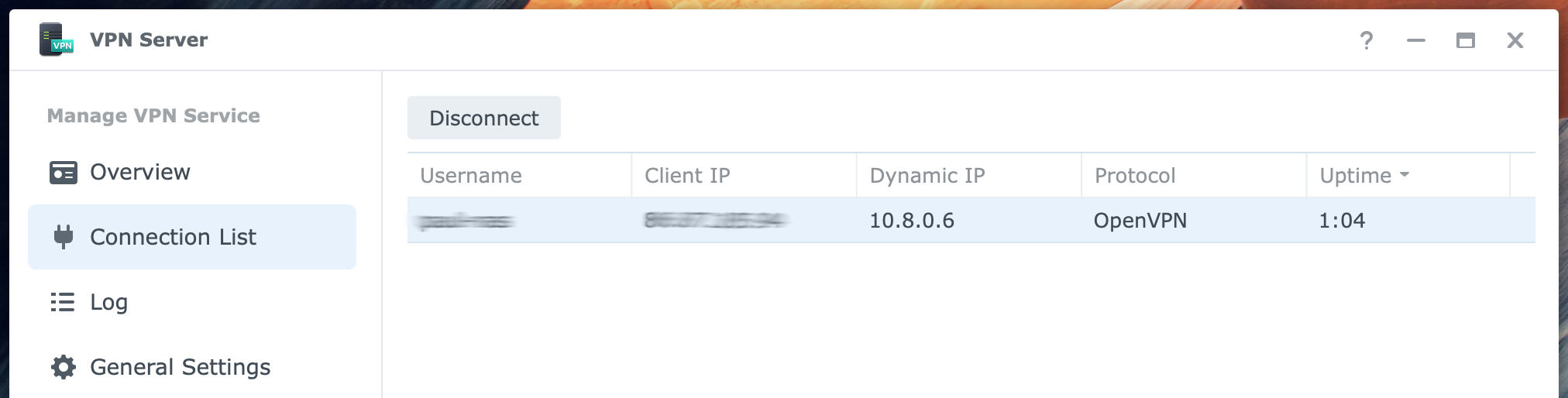
Go to Connection List to see the current connections. Notice the refresh icon in the bottom-right corner. On this page, you see which users are connected, how long, and which protocol they use. If necessary, you can disconnect with the Disconnect button at the top. Disconnecting can be helpful if a connection gets stuck, preventing the user from connecting again.
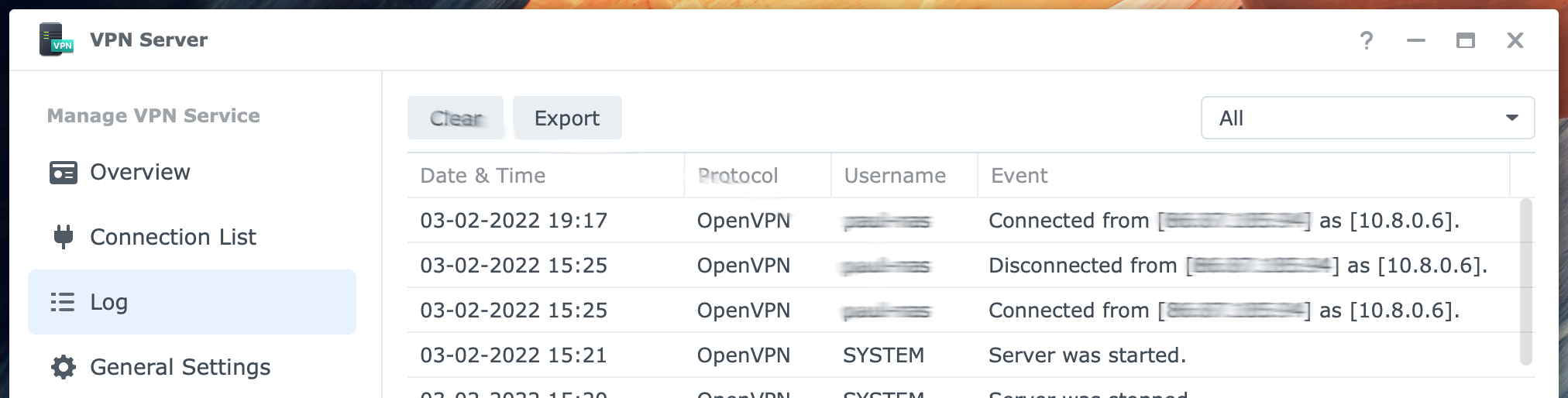
Go to Log to see the VPN server log. The log shows similar information to the connection list but includes a history. You can clear and export the log. You can filter the log per protocol from the drop-down list in the top-right corner to make browsing through the events easier.
Monitor the VPN Connect client
It can happen that you cannot connect to the VPN server of the NAS. The OpenVPN Connect app on your computer can generate different error messages. I show them below with an explanation.
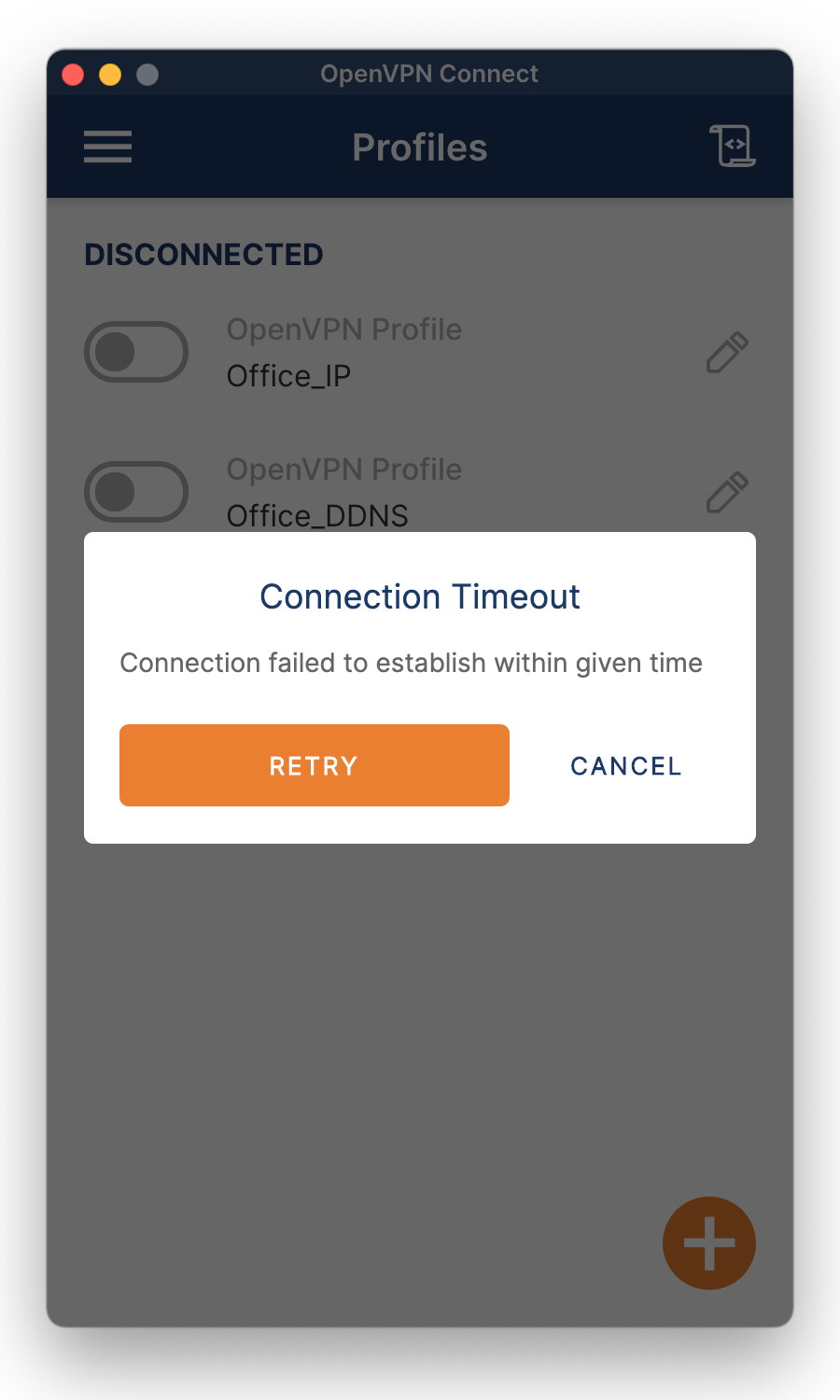
A Connection Timeout means that the VPN client could not connect to the VPN server. A timeout happens if the VPN server is not running, the router does not forward traffic properly, or the IP address or DNS name the client attempts to connect to does not listen to the assigned port.
Check the VPN server, router configuration, the external IP address, or (D)DNS name.
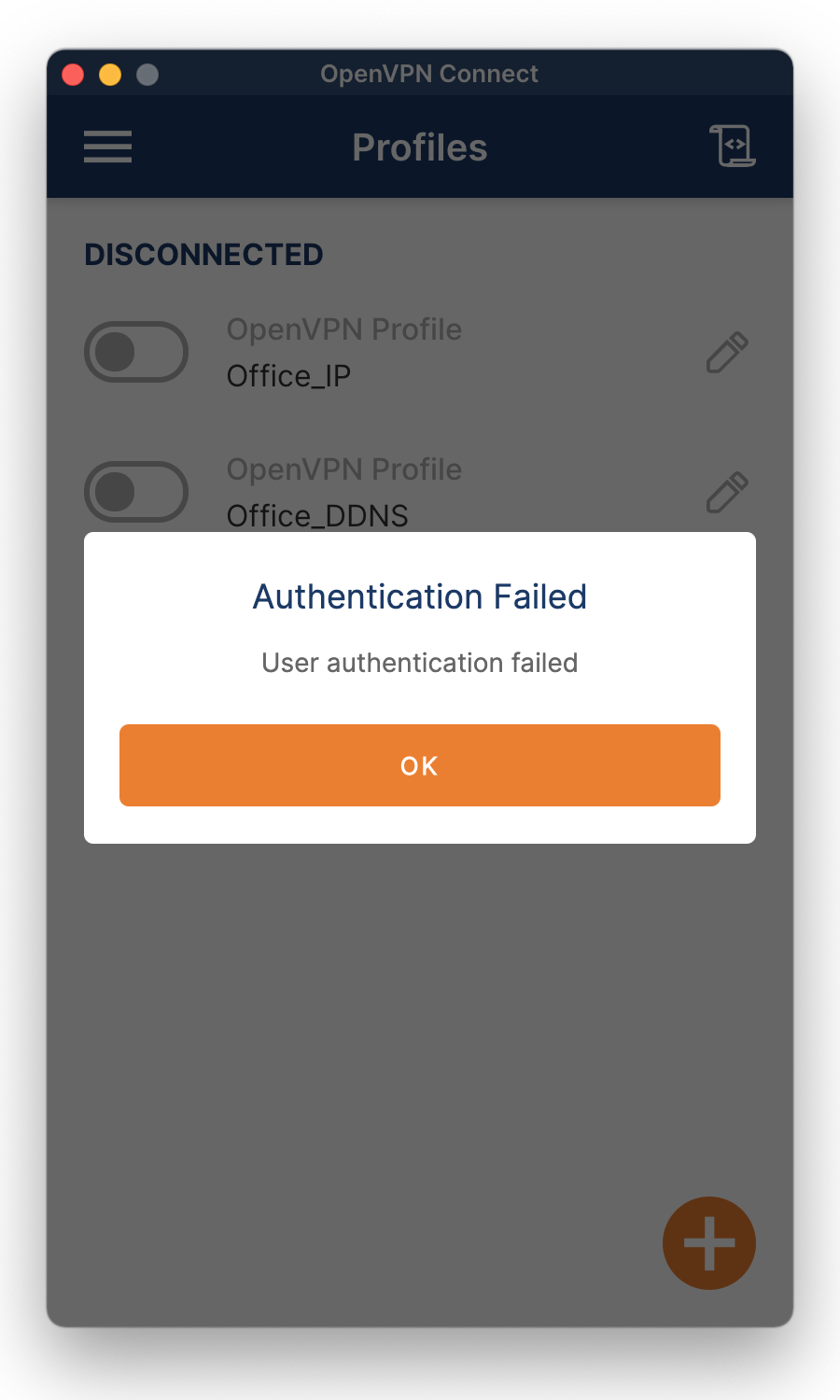
An Authentication Failed message means a successful connection with the VPN server, but the user authentication failed. Possible causes are that the user has no privilege for the link, has too many connections, or has too many connections in total for the VPN server. A wrong password is also a possibility.
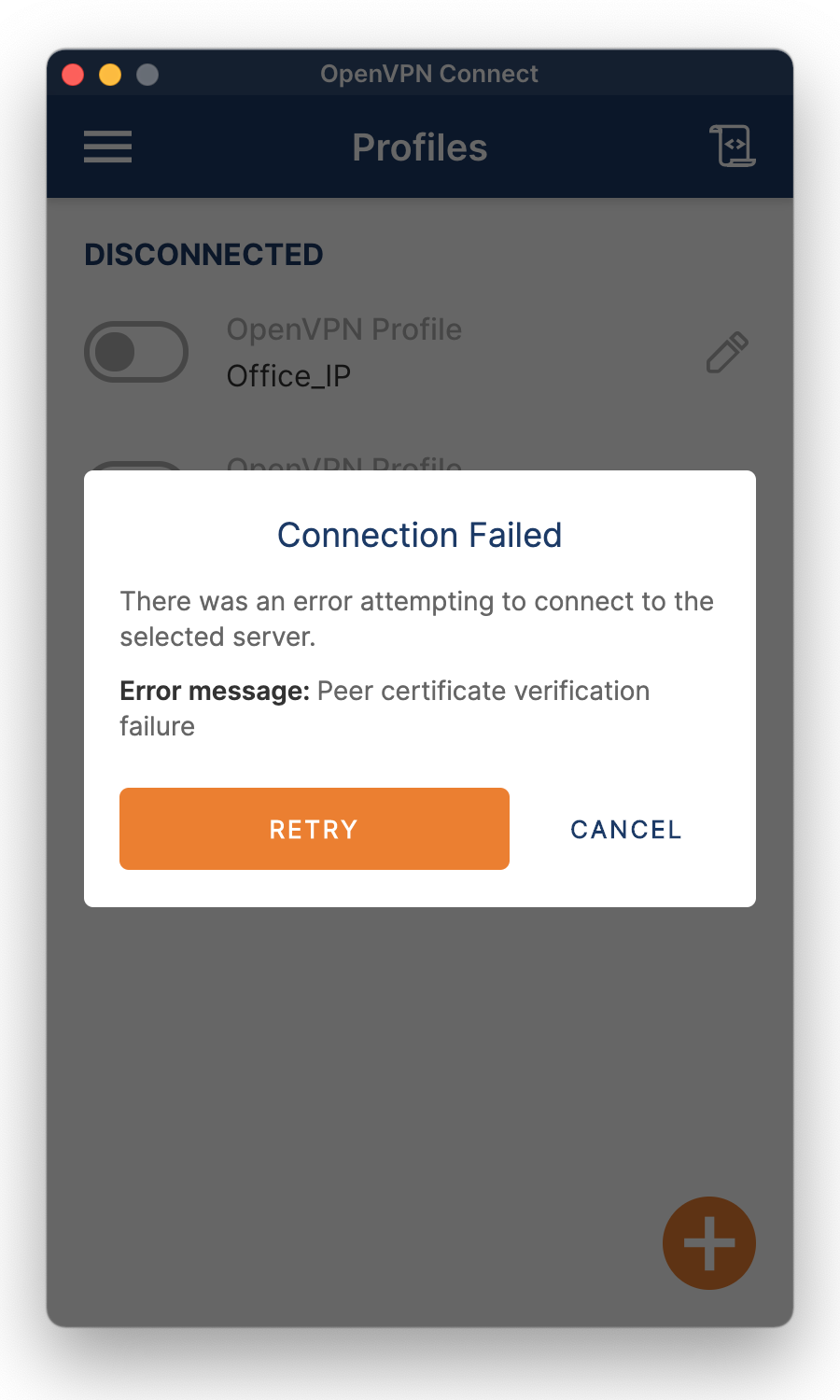
The Connection Failed message means that there initially was a connection but it was dropped immediately. The explanation is in the error message. It is about a certificate. Both the VPN Server on the NAS and the VPN client on the computer have a certificate, and they are peers.
This error occurs when the certificates do not correlate. A possible cause is that the certificate for the VPN Server on the NAS is changed since the connection details for the VPN connection were exported.
To solve the issue, export the connection details again and reconfigure the VPN connection on the VPN client.
The OpenVPN Connect client has a built-in log. Click on the icon in the top-right corner to open the log.
The log is quite extensive and can be overwhelming. It can be helpful for an experienced administrator to solve any issues you may have.
Troubleshoot your connection
To wrap up monitoring and troubleshooting, some tips to solve issues with your connection.
- Is the computer with the VPN client connected to the internet? Note that a local network connection does not guarantee access to the internet. Browse a popular website, or go to https://myip.com to read your external address as this gives a good indication of a healthy connection to the internet.
- Is the IP address the VPN client connects to still valid? The external IP address of your destination site can have changed. When this happens, the connection fails. On the side of the VPN Server and NAS, go to https://myip.com and compare the address with the one configured in the VPN client.
- If you connect to a DDNS name, is the DDNS service still active? Check the DDNS set up on the NAS, assuming you use that service from the NAS.
- Are you the only one who has connection problems, assuming you have coworkers? Maybe you have a VPN client installed on a smartphone or tablet. Try to connect from one of these devices to see if that works.
- Is the port forwarding in the internet router on the destination site still active? Does it point towards the right IP address of the VPN Server, in our case also the NAS?
- Is the NAS still up and running? Is the VPN server on the NAS still up and running? The NAS might be hibernating. Wait a minute and try again.
Thanks for reading
This post is donation-ware, and I made it to help you. If it did, please consider leaving a comment or even buying me a coffee. I will be eternally grateful.
Paul Steunebrink / Storage Alchemist